|
History > 2009 > USA > Internet (I)
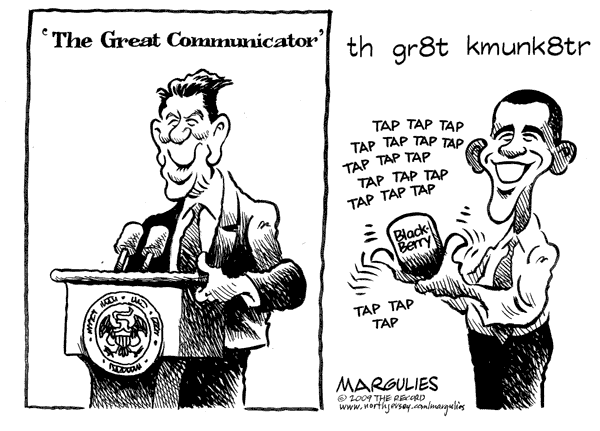
Jimmy Margulies
political cartoon
New Jersey -- The Record
Cagle
24 January 2009
L to R :
Ronald Reagan, Barack H. Obama
Google Adds Live Updates to Results
December 8, 2009
The New York Times
By BRAD STONE
MOUNTAIN VIEW, Calif. — Unveiling significant changes to its dominant search
engine on Monday, Google said it would begin supplementing its search results
with the updates posted each second to sites like Twitter, Facebook and MySpace.
As part of its much-anticipated entrance into the field known as real-time
search, Google said that over the next few days its users would begin seeing
brand-new tweets, blog items, news articles and social networking updates in
results for certain topical searches.
Previously it took a few minutes for updates from social networks and blogs to
filter into Google’s results.
“Clearly in today’s world, that’s not fast enough,” Amit Singhal, a Google
fellow, said at a press conference at the Computer History Museum here.
“Information is being posted at a pace we’ve never seen before, and in this
environment, seconds matter.”
A search for “Copenhagen” on Google, for instance, where global climate talks
are under way, produces the standard Web results, but with a box in the middle
of the page where blog items, press releases, news articles and tweets scroll
past.
The box updates every few seconds. A tweet from Tom Nguyen (@tomng) in the Bay
Area read: “It’s snowing in North Beach. Explain that, Copenhagen.” Searching
for “Pearl Harbor” on Monday, the 68th anniversary of the attack, turned up
tweets from people who were memorializing those who died there, while the live
results for “Tiger Woods” were less family-friendly.
Google struck formal partnerships with Twitter, Facebook and MySpace to quickly
bring updates from those services into its search index. The companies did not
disclose terms of those deals. Facebook has said publicly it is not earning
money from the deal, and is giving Google updates only from the public profile
pages on the service, which can already be seen by anyone on the Web.
Twitter makes a search tool available on its own site. But Biz Stone, a Twitter
co-founder, said that Google would be better able to provide Tweets that were
relevant to a particular user’s questions. “We’re not good at relevancy right
now, and they are,” he said. “More people will get more value out of Twitter
because we are doing this with Google.”
Twitter has also struck a separate deal with Microsoft to make live updates
available in the Bing search engine.
The new Google features are likely to be most useful for breaking news events
like earthquakes, when people want constantly updated information without having
to scan multiple sources, said Danny Sullivan, editor of the blog Search Engine
Land.
In other situations, Mr. Sullivan said, the live scrolling is likely to be
little more than diversions, since the information was always present in Google
search results but just took slightly longer to get there.
Google introduced several other products at its event on Monday. The most
ambitious, called Google Goggles, allows people to send Google a cellphone
photograph of, say, a landmark or a book, and have information about the
contents of the image returned to them instantly.
The technology has one potentially provocative use: someone could conceivably
send Google a photo of a person — if they fail to remember an acquaintance’s
name, for example — and get enough information about him or her to avoid an
awkward encounter.
But Google said image recognition technology would have to improve and the
privacy implications would have to be more fully considered before it would make
that possible. Google Goggles works on phones running Google’s Android operating
system and will be available for other phones soon.
Google also outlined developments in voice search, which will make it easier for
people to search the Web from a mobile phone. It said it would now allow people
to speak their queries to Google in Japanese, in addition to English and
Chinese. The company plans to add new languages next year.
Demonstrating the feature, a Japanese-speaking Google employee spoke a long
query into a Motorola Droid phone, asking for the best restaurants near Google’s
offices in Tokyo. In response, the Droid phone returned a detailed map of the
area, with restaurants pinpointed on the page.
“We are just in the third decade of the personal computer revolution, and it may
be only now that our eyes open to what the possibilities may be,” said Vic
Gundotra, a vice president for engineering at Google, citing improvements in
wireless connectivity and Internet services. Mr. Gundotra also demonstrated a
tool that would let a person speak a request into her phone in English and have
it read back in another language. He said the feature could be introduced next
year.
Google Adds Live Updates
to Results, NYT, 8.12.2009,
http://www.nytimes.com/2009/12/08/technology/companies/08google.html
Google Allows Limits
on Free News Access
December 2, 2009
Filed at 6:41 a.m. ET
The New York Times
By THE ASSOCIATED PRESS
LONDON (AP) -- Google (NASDAQ:GOOG) Inc. is allowing publishers of paid
content to limit the number of free news articles accessed by people using its
Internet search engine, a concession to an increasingly disgruntled media
industry.
There has been mounting criticism of Google's practices from media publishers --
most notably News Corp. (NASDAQ:NWS) chairman and chief executive Rupert Murdoch
-- that argue the company is profiting from online news pages.
In an official blog posted late Tuesday, Josh Cohen, Google's senior business
product manager, said the company had updated its so-called First Click Free
program so publishers can limit users to viewing no more than five articles a
day without registering or subscribing.
Previously, each click from a user of Google's search engine would be treated as
free.
"If you're a Google user, this means that you may start to see a registration
page after you've clicked through to more than five articles on the website of a
publisher using First Click Free in a day ... while allowing publishers to focus
on potential subscribers who are accessing a lot of their content on a regular
basis," Cohen said in the post.
Murdoch on Tuesday told a Washington D.C. conference that media companies should
charge for content and stop news aggregators like Google from "feeding off the
hard-earned efforts and investments of others."
News Corp. already charges for online access to The Wall Street Journal and it
plans to expand that to other publications, including British newspapers The Sun
and The Times.
A fundamental problem facing the media industry, Murdoch told the U.S. Federal
Trade Commission workshop, is that "technology makes it cheap and easy to
distribute news for anyone with Internet access, but producing journalism is
expensive."
"Right now there is a huge gap in costs," he added, referring to news
compilation sites like Google.
Cohen stressed that publishers and Google could coexist, with the former able to
charge for their content and still make it available via Google under the
revamped click program.
"The two aren't mutually exclusive," Cohen said on the blog.
"After all, whether you're offering your content for free or selling it, it's
crucial that people find it," he added. "Google can help with that."
Cohen said that Google will also begin crawling, indexing and treating as "free"
any preview pages -- usually the headline and first few paragraphs of a story --
from subscription websites.
People using Google would then see the same content that would be shown free to
a user of the media site and the stories labelled as "subscription" in Google
News.
"The ranking of these articles will be subject to the same criteria as all sites
in Google, whether paid or free," Cohen said. "Paid content may not do as well
as free options, but that is not a decision we make based on whether or not it's
free. It's simply based on the popularity of the content with users and other
sites that link to it."
Google Allows Limits on
Free News Access, NYT, 2.12.2009,
http://www.nytimes.com/aponline/2009/12/02/business/AP-EU-Google-FreeNews.html
Internet Addresses Can Use New Scripts
October 31, 2009
The New York Times
By CHOE SANG-HUN
SEOUL — By the middle of next year, Internet surfers will be allowed to use
Web addresses written completely in Chinese, Arabic, Korean and other languages
using non-Latin alphabets, the organization overseeing Internet domain names
announced Friday in a decision that could make the Web more accessible.
In an action billed as one of the biggest changes in the Web’s four-decade
history, the board of the Internet Corporation for Assigned Names and Numbers —
or Icann — voted Friday during its annual meeting, held in Seoul, to allow such
scripts in Internet addresses.
The decision is a “historic move toward the internationalization of the
Internet,” said Rod Beckstrom, Icann’s president and chief executive. “We just
made the Internet much more accessible to millions of people in regions such as
Asia, the Middle East and Russia.”
This change affects domain names — anything that comes after the dot, including
.com, .cn or .jp. Domain names have been limited to 37 characters — 26 Latin
letters, 10 digits and a hyphen. But starting next year, domain names can
consist of characters in any language. In some Web addresses, non-Latin scripts
are already used in the portion before the dot. Thus, Icann’s decision Friday
makes it possible, for the first time, to write an entire Internet address in a
non-Latin alphabet.
Initially, the new naming system will affect only Web addresses with “country
codes,” the designators at the end of an address name, like .kr (for Korea) or
.ru (for Russia). But eventually, it will be expanded to all types of Internet
address names, Icann said.
Some security experts have warned that allowing internationalized domain names
in languages like Arabic, Russian and Chinese could make it more difficult to
fight cyberattacks, including malicious redirects and hacking. But Icann said it
was ready for the challenge.
“I do not believe that there would be any appreciable difference,” Mr. Beckstrom
said in an interview. “Yes, maybe some additional potential but at the same
time, some new security benefits may come too. If you look at the global set of
cybersecurity issues, I don’t see this as any significant new threat if you look
at it on an isolated basis.”
The decision, reached after years of testing and debate, clears the way for
Icann to begin accepting applications for non-Latin domain names Nov. 16. People
will start seeing them in use around mid-2010, particularly in Arabic, Chinese
and other scripts in which demand for the new “internationalized” domain name
system has been among the strongest, Icann officials say.
Internet addresses in non-Latin scripts could lead to a sharp increase in the
number of global Internet users, eventually allowing people around the globe to
navigate much of the online world using their native language scripts, they
said.
This is a boon especially for users who find it cumbersome to type in Latin
characters to access Web pages. Of the 1.6 billion Internet users worldwide,
more than half use languages that have scripts that are not based on the Latin
alphabet.
Hong Jong-gil, an Internet industry analyst at Korea Investment and Securities
in Seoul, said the new names would help children and old people who had not
learned the Latin alphabet. But he did not foresee any major increase in the
number of Internet users because Internet penetration has less to do with
whether one has to type in English-alphabet domain names and more to do with
“whether you can afford a PC and your community has broadband access.”
Agencies that help companies and individuals get Internet domains welcomed the
Icann decision, noting it would be good for their own businesses.
“This is great news for us. This opens a new demand for domain names,” said Yang
Eun-hee, an official at Gabia.com, an Internet domain agency. “There will be a
rush among businesses to get new local-language Web addresses to protect their
brand names. These days, a big company typically has dozens or hundreds of
domains for their products, and it will be quite a cost to get all the new
names.”
Observers agree that the change could make a difference for many businesses. “A
lot of companies will end up having double domains — the existing one in English
and a new one in the local script,“ said Choi Kyoung-jin, an analyst at Shinhan
Investment. “A Korean domain name may be useful for Koreans but it’s not for
foreign customers.”
Users who do not use the Latin alphabet can now reach Web sites by asking search
engines to provide their links.
But a change in the domain name policy has become inevitable, Internet industry
officials said. For example, there are so many .com Web addresses that it has
become next to impossible to find an English word or an intelligible combination
of two English words not already in use, they said.
“Today’s decision opens up a whole new Internet territory,” Ms. Yang said. “The
Internet will become more multi-lingual than before.”
Internet Addresses Can
Use New Scripts, NYT, 31.10.2009,
http://www.nytimes.com/2009/10/31/technology/31net.html
Facebook and Google Expected to Offer Music
October 22, 2009
The New York Times
By BRAD STONE
SAN FRANCISCO — Music fans are about to get two new ways to find and sample
songs on the Web, as Google and Facebook introduce new features on their
services.
Google, the search giant, plans to announce a music initiative at an event it
will hold at the Capitol Records building in Hollywood next Wednesday, according
to three people briefed on the details, who asked for anonymity because they
were not authorized to talk about the service before it was announced.
The service will give users a more efficient way to find, learn about and sample
music after they search for information about bands, albums or songs, said a
person who has seen an early demonstration.
Google, based in Mountain View, Calif., will not host any music, nor has it
forged any new relationships with the major music labels. But it has struck
deals with several streaming music services to let people easily sample music
directly from the search engine.
Through relationships with streaming music sites, like Lala, Imeem and the
MySpace division iLike, users wanting to sample a song will be presented with a
pop-up box from one of the music partners that will play at least a 30-second
sample, and in some cases, the whole song.
Neither Google nor its new partners would comment on the initiative. But an
invitation to an event in Los Angeles, hosted by iLike, Lala and others, was
sent out early Wednesday morning to reporters.
Google is not alone wading into the music business. The social network Facebook,
which has been toying with bringing music to its site for at least a year, will
also take its first step by integrating Lala into its popular gift store,
according to Brandee Barker, a Facebook spokeswoman.
Currently the Facebook gift store is stocked with playful images like birthday
cakes and dogs. People buy these images for a dollar, using 10-cent credits they
must purchase with a credit card. Then they can post these graphics to the
profile pages of their friends. Facebook does not disclose revenue from its gift
store, but it is believed to be a small portion of its overall revenue.
Over the summer, Facebook began limited tests allowing companies like American
Greetings and JibJab, a humor site, to add their virtual wares, like birthday
videos, to the gift store. Facebook, based in Palo Alto, Calif., will gradually
roll out the gift store to users in the next few weeks.
Music from Lala will be part of that effort, said John Kuch, a Lala spokesman.
The service will work for Facebok users in the United States only.
There will be two ways to buy songs: For 10 cents, or one Facebook credit, users
can buy Web songs that can be played by the recipient online in perpetuity. Or
they can pay full price, probably a dollar or 10 credits, then download the song
and transfer it to a music player.
Facebook sees the gift store as a way to obtain the credit card numbers of more
customers and develop a one-click payment mechanism that third-party developers
can later use to sell virtual goods on the applications they are creating for
the site.
Facebook and Google
Expected to Offer Music, NYT, 22.10.2009,
http://www.nytimes.com/2009/10/22/technology/internet/22google.html
Parental Guidance on Web Video for Children
October 8, 2009
The New York Times
By WARREN BUCKLEITNER
If you still need convincing that the digital future has arrived, consider
this: By the time you finish this article, at least 10 more hours of new video
will be uploaded to YouTube. Combine this with a young child’s curiosity and
pocket-size video players, and you get the perfect recipe for parental distress.
After all, what youngster would not want a million channels of TV?
Finding video these days that will hold a child’s attention is far easier than
turning a dial. One or two carefully chosen keywords, like “moonwalking,” can
give your child a moonwalking tutorial, or “rubber ducky,” for a dose of Ernie’s
classic Sesame Street serenade.
For parents who grew up with only a few television channels, the idea of turning
a curious child loose with such a vast amount of content can produce a fair
amount of anxiety. YouTube has a policy banning children under 13 in its fine
print. “YouTube is for teens and adults, not children.” said Scott Rubin, a
YouTube spokesman.
Yet, according to Nielsen VideoCensus, more children under 13 watched videos in
August on YouTube than on Disney.com, Nick.com and Cartoon Network combined.
There is also no shortage of children’s content on YouTube. KidZui.com, a
subscription-based Web portal service, lists no fewer than 60,000 child-friendly
selections on its site.
Parents and teachers are discovering YouTube’s potential for exposing children
to new ideas. Children can learn how to carve a pumpkin or improve their
sketching skills. But it can just as easily expose them to videos of births,
surgeries, corpses and executions — all things conscientious parents might
prefer their children discover at a later age.
In my own town of Flemington, N.J., it is easy to find plenty of YouTube-using
children and cautious parents. When they are not playing on their Wii, the
Liebowitz children, Seth, 5, and Asa, 7, like looking up videos of homemade
skits involving Webkinz, the virtual reality toys, by typing in “Webkinz idol.”
They giggle at the elaborate Evian commercial featuring roller skating babies
(warning: you will giggle, too). None of the parents I interviewed felt
completely safe giving their children free rein on YouTube, however. “I’ve done
my own searches on the topics they look for, just to be sure,” said Brooke
Liebowitz. “Plus, I’m always in the next room.”
They also were not aware of YouTube’s customization features, intended to filter
content or offer prescreened selections to their children. Here’s a tour of how
to make the most of the service’s safety features.
ACTIVATE YOUTUBE’S FILTER While salty language and edgy humor and are
commonplace on YouTube, explicit content is rare. Still, it is smart to test the
waters with a few of your child’s favorite search terms, just to make sure you
are comfortable with what shows up.
Make sure you scroll down to the comments, which is usually where offensive
vocabulary appears. You can bleep out these comments automatically. Look at the
top of the text comments column, and choose options. This leads to a set of
preferences that includes “hide objectionable words.” Once clicked, it will
replace offending words with rows of asterisks, before your child sees them.
Your preferences will remain in place as long as you use the same browser.
UPLOAD YOUR OWN VIDEO As a YouTube content provider, you quickly learn what you
can and can’t do. This experience will help you and is an effective way to
better understand how the process works.
BE A HALL MONITOR Notice some nasty content? YouTube makes tattling easy. When
you are on the site, look for the word flag below every video. Give it a click,
and you can send the video to the YouTube screeners.
This self-cleansing process can help keep bad surprises away from other people’s
children, but it obviously isn’t perfect. YouTube’s Advance Search options also
include the ability to prevent videos that have been tagged as explicit by the
screeners, like news film of a suicide bombing, for example, from showing up in
your child’s search results in the first place. For more details, explore the
links at the bottom of the home page, including the YouTube safety center
KEEP UP WITH TRENDS To stay abreast of the bus stop conversation, you can use
YouTube’s counters to keep up with the most-viewed videos. Here’s how.
From the home page, click videos, and then most viewed, and then look for the
word “when” and select a time option. You’ll see that “Evolution of Dance,” a
comedy routine in which Judson Laipply demonstrates various dance moves, has
more than 127 million views.
Other high-ranking videos of interest to your children include Potter Puppet
Pals — puppet versions of Harry Potter characters — in “The Mysterious Ticking
Noise” (69 million views) and Animation vs. Animator, a stick-figure cartoon
(almost five million views).
Be just as aware of options outside YouTube. Sources of streaming video content
for children continue to grow beyond YouTube’s servers. TV Guide’s Web site
lists almost 900 full episodes of online children’s programs. Sources include
Comcast’s Kabillion (kabillion.com/videos/) and Hulu
(hulu.com/channels/Family/Kids).
LEAVE THE SORTING TO PROS A growing number of sites are powered by YouTube, but
operate independently. Two of the best are ZuiTube.com, with a library of 60,000
videos, and the Totlol.com, a Canadian site that can be customized by age. Both
are free, with subscription options. Another, called Kideos.com, offers fewer
choices, but a cleaner interface.
GET YOUTUBE’S CHANNELS Besides steering your child toward preselected,
high-interest videos, you can create an activity feed, which is a running list
of the latest action on any channel you have subscribed to. Because your channel
can be embedded outside of YouTube — in blogs, Facebook pages or Twitter — news
of fresh video uploads can spread faster.
To find channels, start with something your child is passionate about. Animals?
Try your local zoo’s page. Here’s the Houston Zoo channel:
youtube.com/user/houstonzoo. Cartoon lovers can watch episodes like Pokémon and
Yu-Gi-Oh at the 4Kids channel youtube.com/user/4KidsTV.
SHOW CHILDREN HOW TO VOTE At its heart, YouTube is a popularity contest, and
your child can be the critic, writing informed reviews, posting ratings and
choosing who deserves a subscription.
In addition, he or she can start to collect and share favorite videos by making
playlists, which differ from YouTube Channels because they can contain videos
from a variety of places. To learn how to make a playlist, such as one on train
lore, you can watch a video (on YouTube, naturally) at bit.ly/12flaY. LET THEM
WRITE Offering a review includes writing, which has little value unless someone
else can read it. Teachers call this authentic publishing, and YouTube is a gold
mine of opportunity for sharpening spelling and editing. It can even build
acting skills, as children make homework projects like a third grader’s video
tour of Des Moines at bit.ly/3aZumM.
Letting a child stumble at random into something as vast as YouTube can be akin
to letting them explore a public park unsupervised. It can be enlightening, but
it’s wise to stay a few steps ahead of your child’s curiosity and make
discoveries together. Consider it an essential parenting skill for the 21st
century.
Parental Guidance on Web
Video for Children, NYT, 8.10.2009,
http://www.nytimes.com/2009/10/08/technology/personaltech/08basics.html
By Degrees
Plugged-In Age Feeds a Hunger for Electricity
September 20, 2009
The New York Times
By JAD MOUAWAD and KATE GALBRAITH
With two laptop-loving children and a Jack Russell terrier hemmed in by an
electric fence, Peter Troast figured his household used a lot of power. Just how
much did not really hit him until the night the family turned off the overhead
lights at their home in Maine and began hunting gadgets that glowed in the dark.
“It was amazing to see all these lights blinking,” Mr. Troast said.
As goes the Troast household, so goes the planet.
Electricity use from power-hungry gadgets is rising fast all over the world. The
fancy new flat-panel televisions everyone has been buying in recent years have
turned out to be bigger power hogs than some refrigerators.
The proliferation of personal computers, iPods, cellphones, game consoles and
all the rest amounts to the fastest-growing source of power demand in the world.
Americans now have about 25 consumer electronic products in every household,
compared with just three in 1980.
Worldwide, consumer electronics now represent 15 percent of household power
demand, and that is expected to triple over the next two decades, according to
the International Energy Agency, making it more difficult to tackle the
greenhouse gas emissions responsible for global warming.
To satisfy the demand from gadgets will require building the equivalent of 560
coal-fired power plants, or 230 nuclear plants, according to the agency.
Most energy experts see only one solution: mandatory efficiency rules specifying
how much power devices may use.
Appliances like refrigerators are covered by such rules in the United States.
But efforts to cover consumer electronics like televisions and game consoles
have been repeatedly derailed by manufacturers worried about the higher cost of
meeting the standards. That has become a problem as the spread of such gadgets
counters efficiency gains made in recent years in appliances.
In 1990, refrigerator efficiency standards went into effect in the United
States. Today, new refrigerators are fancier than ever, but their power
consumption has been slashed by about 45 percent since the standards took
effect. Likewise, thanks in part to standards, the average power consumption of
a new washer is nearly 70 percent lower than a new unit in 1990.
“Standards are one of the few ways to cheaply go after big chunks of energy
savings,” said Chris Calwell, a founder and senior researcher at Ecos, a
consulting firm that specializes in energy efficiency.
Part of the problem is that many modern gadgets cannot entirely be turned off;
even when not in use, they draw electricity while they await a signal from a
remote control or wait to record a television program.
“We have entered this new era where essentially everything is on all the time,”
said Alan Meier, a senior scientist at the Lawrence Berkeley National Laboratory
and a leading expert on energy efficiency.
People can, of course, reduce this waste — but to do so takes a single-minded
person.
Mr. Troast, of South Freeport, Me., is just the kind of motivated homeowner
willing to tackle such a project. His day job is selling energy efficiency
equipment through an online business. He was not put off by the idea of hunting
behind cabinets to locate every power supply and gadget, like those cable boxes,
Web routers or computers that glowed in the dark.
The Troasts cut their monthly energy use by around 16 percent, partly by
plugging their computers and entertainment devices into smart power strips. The
strips turn off when the electronics are not in use, cutting power consumption
to zero.
While Mr. Troast’s experience demonstrates that consumers can limit the power
wasted by inactive devices, another problem is not as easily solved: many
products now require large amounts of power to run.
The biggest offender is the flat-screen television. As liquid crystal displays
and plasma technologies replace the old cathode ray tubes, and as screen sizes
increase, the new televisions need more power than older models do. And with all
those gorgeous new televisions in their living rooms, Americans are spending
more time than ever watching TV, averaging five hours a day.
The result is a surge in electricity use by TVs, which can draw more power in a
year than some refrigerators now on the market.
Energy experts say that manufacturers have paid too little attention to the
power consumption of televisions, in part because of the absence of federal
regulation.
Another power drain is the video game console, which is found in 40 percent of
American households. Energy experts — and many frustrated parents — say that
since saving games is difficult, children often keep the consoles switched on so
they can pick up where they left off.
Noah Horowitz, at the Natural Resources Defense Council, calculated that the
nation’s gaming consoles, like the Xbox 360 from Microsoft and the Sony
PlayStation 3, now use about the same amount of electricity each year as San
Diego, the ninth-largest city in country.
Mandatory efficiency standards for electronic devices would force manufacturers
to redesign their products, or spend money adding components that better control
power use.
Many manufacturers fight such mandates because they would increase costs, and
they also claim the mandates would stifle innovation in a fast-changing
industry.
The government has never aggressively tackled the television issue because of
opposition from the consumer electronics lobby in Washington, experts say. In
1987, before televisions had swelled into such power hogs, Congress gave the
Energy Department — which generally carries out the standards — the option of
setting efficiency rules for TVs.
But industry opposition derailed an effort in the 1990s to use that authority,
according to Steve Nadel of the American Council for an Energy-Efficient
Economy. A more recent attempt to require home electronics to use no more than
one watt of power in standby mode met the same fate. The federal government has
moved forward on only two standards for electronics, covering battery chargers
and external power supplies.
In the absence of federal action, a few states have moved on their own. The
California Energy Commission just proposed new standards for televisions that
would cut their power consumption in half by 2013. But that effort has set off a
storm of protest from manufacturers and their trade group, the Consumer
Electronics Association. (It is still expected to pass, in November.)
A spokesman for the industry said that government regulations could not keep up
with the pace of technological change.
“Mandates ignore the fundamental nature of the industry that innovates due to
consumer demand and technological developments, not regulations,” said Douglas
Johnson, the senior director of technology policy at the association.
Mr. Johnson said that California’s limits on manufacturers, which he called
arbitrary, might delay or even prohibit some features of new devices. Instead,
he praised the government’s voluntary Energy Star program, which he says
encourages efficiency without sacrificing innovation.
“Mandatory limits, such as we see in California, threaten to raise prices for
consumers and reduce consumer choice,” he said.
Estimates vary regarding how much a mandatory efficiency program for gadgets
would cost consumers. For some changes, like making sure devices draw minimal
power in standby mode, experts say the cost may be only a few extra cents. At
the other extreme, the most energy-efficient of today’s televisions can cost
$100 more than the least energy-efficient. (That expense would be partly offset
over time, of course, by lower power needs.)
Some types of home electronics are rated under Energy Star, a program that
classifies products in more than 60 categories according to their energy
consumption. But that program, while a boon to conscientious consumers who buy
only the most efficient products, does not prevent the sale of wasteful devices
and has not succeeded in driving them off the market.
The lack of regulation of gadgets is a notable contrast to the situation with
appliances.
Congress adopted the nation’s first electrical efficiency standards in the
1980s, focusing initially on kitchen and other large appliances. That effort
made some steep gains, particularly for refrigerators, which were once among the
biggest power hogs in a typical home.
The federal effort lagged during the administration of George W. Bush, and the
Energy Department missed a string of deadlines set by Congress. But the Obama
administration has vowed to make maximum use of existing law, speeding up the
adoption of 26 standards on a host of products that include microwave ovens and
clothes dryers. Tougher lighting standards, embraced by both the Bush and Obama
administrations, are due to take effect in coming years.
But Congress has never granted any administration the authority to set standards
for power-hogging electronic gadgets like game consoles and set-top boxes. Even
now, when both the administration and Congress are focused on the nation’s
energy problems, no legislation is moving forward to tackle the issue.
Experts like Dan W. Reicher, who directs Google’s energy efforts, argue that the
United States must do better, setting an example for the rest of the world.
“If we can’t improve the efficiency of simple appliances and get them into
greater use,” Mr. Reicher said, “it’s hard to believe that we’ll succeed with
difficult things like cleaning up coal-fired power plants.”
Plugged-In Age Feeds a
Hunger for Electricity, NYT, 20.9.2009,
http://www.nytimes.com/2009/09/20/business/energy-environment/20efficiency.html
Pentagon Keeps Wary Watch as Troops Blog
September 9, 2009
The New York Times
By JAMES DAO
Over the course of 10 months in eastern Afghanistan, an Army specialist
nicknamed Mud Puppy maintained a blog irreverently chronicling life at the
front, from the terror of roadside bombs to the tyrannies of master sergeants.
Often funny and always profane, the blog, Embrace the Suck (military slang for
making the best of a bad situation), flies under the Army’s radar. Not
officially approved, it is hidden behind a password-protected wall because the
reservist does not want his superiors censoring it.
“Some officer would be reviewing all my writing,” the 31-year-old soldier, who
insisted that his name not be used, said in an e-mail message. “And sooner or
later he would find something to nail me with.”
There are two sides to the military’s foray into the freewheeling world of the
interactive Web. At the highest echelons of the Pentagon, civilian officials and
four-star generals are newly hailing the power of social networking to make
members of the American military more empathetic, entice recruits and shape
public opinion on the war.
Gen. Ray Odierno, commander of American forces in Iraq, is on Facebook. The
chairman of the Joint Chiefs of Staff, Adm. Mike Mullen, has a YouTube channel
and posts Twitter updates almost daily.
The Army is encouraging personnel of all ranks to go online and collaboratively
rewrite seven of its field manuals. And on Aug. 17, the Department of Defense
unveiled a Web site promoting links to its blogs and its Flickr, Facebook,
Twitter and YouTube sites.
The Web, however, is a big place. And the many thousands of troops who use
blogs, Facebook, Twitter and other social media sites to communicate with the
outside world are not always in tune with the Pentagon’s official voice.
Policing their daily flood of posts, videos and photographs is virtually
impossible — but that has not stopped some in the military from trying.
The Department of Defense, citing growing concerns about cybersecurity, plans to
issue a new policy in the coming weeks that is widely expected to set
departmentwide restrictions on access to social networking sites from military
computers. People involved with the department’s review say the new policy may
limit access to social media sites to those who can demonstrate a clear work
need, like public information officers or family counselors.
If that is the case, many officials say, it will significantly set back efforts
to expand and modernize the military’s use of the Web just as those efforts are
gaining momentum. And while the new policy would not apply to troops who use
private Internet providers, a large number of military personnel on bases and
ships across the world depend on their work computers to gain access to the
Internet.
To many analysts and officers, the debate reflects a broader clash of cultures:
between the anarchic, unfiltered, bottom-up nature of the Web and the
hierarchical, tightly controlled, top-down tradition of the military.
“We as an institution still haven’t come to grips with how we want to use
blogging” and other social media, said Lt. Gen. William B. Caldwell IV, the
commander of the Army Combined Arms Center at Fort Leavenworth, Kan.
One of the Army’s leading advocates for more open access to the Web, General
Caldwell argues that social networking allows interaction among enlisted
soldiers, junior officers and generals in a way that was unthinkable a decade
ago.
He requires students at the Command and General Staff College at Fort
Leavenworth to blog, and the college now sponsors 40 publicly available blogs,
including his own, where policies are freely debated.
But getting approval for those blogs, as well as for YouTube and Facebook access
at the college, was a struggle. “At every corner, someone cited a regulation,”
General Caldwell said. In recent months, however, “the Army has made quantum
leaps” in embracing the Web, he added.
Noah Shachtman, editor of Wired.com’s national security blog, Danger Room, which
has reported extensively on the new policy review, said he recently asked
students at West Point whether they would allow soldiers to blog. Almost every
cadet said no.
“Then I asked, ‘How many of you think you can stop the flow of information from
your soldiers?’ ” Mr. Shachtman recalled. “Everybody agreed there is no way to
stop this information from going out anyway. So there is this sort of
dual-headedness.”
Skeptics of the Pentagon review say it is motivated partly by a desire among
certain officials to exert control over the voices of troops on the Web.
Since the advent of military blogging during the Iraq war, some commanders have
remained uncomfortable with the art form, citing concerns about both security
and decorum.
Over the years, blogs have been censored or shut down, and several years ago the
Army instituted requirements that bloggers register with their commanding
officers and submit posts for review. As a result, some bloggers say, blogs have
become tamer — or, as in the case of Mud Puppy’s blog, gone underground.
Officials knowledgeable about the review say it is a result of growing concerns
at the United States Strategic Command, which oversees the military’s use of the
Internet, that social networking sites make military computers vulnerable to
viruses, hackers, identity thieves, terrorists and even hostile governments.
(Those concerns are not focused on the military’s secure system for classified
material, which does not use the public Internet.)
The review may already be having a chilling effect. The Marine Corps recently
restated a ban on using any social media on its network. And the Army, which in
June gave some bases access to Facebook, Twitter and other networking sites,
recently urged units to avoid creating new social media pages until the final
department policy was issued.
Still, even as they consider restricting the troops’ access to social media, the
most senior Pentagon officials have clearly come to view Facebook, Twitter,
YouTube and blogging as crucial elements of their public information operations.
“This department, I think, is way behind our curve” in using social media,
Secretary of Defense Robert M. Gates said in July as he extolled the use of
Twitter by Iranian dissidents.
To critics, the Pentagon’s social media sites are goofy at best, propagandistic
at worst. “It’s like your parents’ using modern slang and failing miserably,”
said Sgt. Selena Coppa, who writes a blog, Active Duty Patriot, which frequently
criticizes the Iraq war and, she says, has gotten her into trouble with her
superiors.
But to many troops, the deeper question is whether the military will allow
personnel in the field to use the sites the Pentagon itself wants to exploit.
For a generation raised on the Web, any restrictions will damage morale, those
people say.
“What comes out of my blog is the experiences of a soldier right in the middle
of all of this,” Mud Puppy (a nickname for military police), who recently
returned home to Illinois, wrote in a recent e-mail message. “I think that
people need to hear from us, more than they need to hear from the big whigs. War
has a cost, and that cost is paid by soldiers.”
Pentagon Keeps Wary
Watch as Troops Blog, NYT, 9.9.2009,
http://www.nytimes.com/2009/09/09/us/09milblogs.html
Cyberwar
Defying Experts, Rogue Computer Code Still Lurks
August 27, 2009
The New York Times
By JOHN MARKOFF
It is still out there.
Like a ghost ship, a rogue software program that glided onto the Internet last
November has confounded the efforts of top security experts to eradicate the
program and trace its origins and purpose, exposing serious weaknesses in the
world’s digital infrastructure.
The program, known as Conficker, uses flaws in Windows software to co-opt
machines and link them into a virtual computer that can be commanded remotely by
its authors. With more than five million of these zombies now under its control
— government, business and home computers in more than 200 countries — this
shadowy computer has power that dwarfs that of the world’s largest data centers.
Alarmed by the program’s quick spread after its debut in November, computer
security experts from industry, academia and government joined forces in a
highly unusual collaboration. They decoded the program and developed antivirus
software that erased it from millions of the computers. But Conficker’s
persistence and sophistication has squelched the belief of many experts that
such global computer infections are a thing of the past.
“It’s using the best current practices and state of the art to communicate and
to protect itself,” Rodney Joffe, director of the Conficker Working Group, said
of the malicious program. “We have not found the trick to take control back from
the malware in any way.”
Researchers speculate that the computer could be employed to generate vast
amounts of spam; it could steal information like passwords and logins by
capturing keystrokes on infected computers; it could deliver fake antivirus
warnings to trick naïve users into believing their computers are infected and
persuading them to pay by credit card to have the infection removed.
There is also a different possibility that concerns the researchers: That the
program was not designed by a criminal gang, but instead by an intelligence
agency or the military of some country to monitor or disable an enemy’s
computers. Networks of infected computers, or botnets, were used widely as
weapons in conflicts in Estonia in 2007 and in Georgia last year, and in more
recent attacks against South Korean and United States government agencies.
Recent attacks that temporarily crippled Twitter and Facebook were believed to
have had political overtones.
Yet for the most part Conficker has done little more than to extend its reach to
more and more computers. Though there had been speculation that the computer
might be activated to do something malicious on April 1, the date passed without
incident, and some security experts wonder if the program has been abandoned.
The experts have only tiny clues about the location of the program’s authors.
The first version included software that stopped the program if it infected a
machine with a Ukrainian language keyboard. There may have been two initial
infections — in Buenos Aires and in Kiev.
Wherever the authors are, the experts say, they are clearly professionals using
the most advanced technology available. The program is protected by internal
defense mechanisms that make it hard to erase, and even kills or hides from
programs designed to look for botnets.
A member of the security team said that the Federal Bureau of Investigation had
suspects, but was moving slowly because it needed to build a relationship with
“noncorrupt” law enforcement agencies in the countries where the suspects are
located.
An F.B.I. spokesman in Washington declined to comment, saying that the Conficker
investigation was an open case.
The first infections, last Nov. 20, set off an intense battle between the hidden
authors and the volunteer group that formed to counter them. The group, which
first called itself the “Conficker Cabal,” changed its name when Microsoft,
Symantec and several other companies objected to the unprofessional connotation.
Eventually, university researchers and law enforcement officials joined forces
with computer experts at more than two dozen Internet, software and computer
security firms.
The group won some battles, but lost others. The Conficker authors kept
distributing new, more intricate versions of the program, at one point using
code that had been devised in academia only months before. At another point, a
single technical slip by the working group allowed the program’s authors to
convert a huge number of the infected machines to an advanced peer-to-peer
communications scheme that the industry group has not been able to defeat. Where
before all the infected computers would have to phone home to a single source
for instructions, the authors could now use any infected computer to instruct
all the others.
In early April, Patrick Peterson, a research fellow at Cisco Systems in San
Jose, Calif., gained some intelligence about the authors’ interests. He studies
nasty computer programs by keeping a set of quarantined computers that capture
and observe them — his “digital zoo.”
He discovered that the Conficker authors had begun distributing software that
tricks Internet users into buying fake antivirus software with their credit
cards. “We turned off the lights in the zoo one day and came back the next day,”
Mr. Peterson said, noting that in the “cage” reserved for Conficker, the
infection had been joined by a program distributing an antivirus software scam.
It was the most recent sign of life from the program, and its silence has set
off a debate among computer security experts. Some researchers think Conficker
is an empty shell, or that the authors of the program were scared away in the
spring. Others argue that they are simply biding their time.
If the misbegotten computer were reactivated, it would not have the
problem-solving ability of supercomputers used to design nuclear weapons or
simulate climate change. But because it has commandeered so many machines, it
could draw on an amount of computing power greater than that from any single
computing facility run by governments or Google. It is a dark reflection of the
“cloud computing” sweeping the commercial Internet, in which data is stored on
the Internet rather than on a personal computer.
The industry group continues to try to find ways to kill Conficker, meeting as
recently as Tuesday. Mr. Joffe said he, for one, was not prepared to declare
victory. But he said that the group’s work proved that government and private
industry could cooperate to counter cyberthreats.
“Even if we lose against Conficker,” he said, “there are things we’ve learned
that will benefit us in the future.”
Defying Experts, Rogue
Computer Code Still Lurks, NYT, 27.8.2009,
http://www.nytimes.com/2009/08/27/technology/27compute.html?hp
Wikipedia to Limit Changes to Articles on People
August 25, 2009
The New York Times
By NOAM COHEN
Wikipedia, one of the 10 most popular sites on the Web, was founded about
eight years ago as a long-shot experiment to create a free encyclopedia from the
contributions of volunteers, all with the power to edit, and presumably improve,
the content.
Now, as the English-language version of Wikipedia has just surpassed three
million articles, that freewheeling ethos is about to be curbed.
Officials at the Wikimedia Foundation, the nonprofit in San Francisco that
governs Wikipedia, say that within weeks, the English-language Wikipedia will
begin imposing a layer of editorial review on articles about living people.
The new feature, called “flagged revisions,” will require that an experienced
volunteer editor for Wikipedia sign off on any change made by the public before
it can go live. Until the change is approved — or in Wikispeak, flagged — it
will sit invisibly on Wikipedia’s servers, and visitors will be directed to the
earlier version.
The change is part of a growing realization on the part of Wikipedia’s leaders
that as the site grows more influential, they must transform its
embrace-the-chaos culture into something more mature and dependable.
Roughly 60 million Americans visit Wikipedia every month. It is the first
reference point for many Web inquiries — not least because its pages often lead
the search results on Google, Yahoo and Bing. Since Michael Jackson died on June
25, for example, the Wikipedia article about him has been viewed more than 30
million times, with 6 million of those in the first 24 hours.
“We are no longer at the point that it is acceptable to throw things at the wall
and see what sticks,” said Michael Snow, a lawyer in Seattle who is the chairman
of the Wikimedia board. “There was a time probably when the community was more
forgiving of things that were inaccurate or fudged in some fashion — whether
simply misunderstood or an author had some ax to grind. There is less tolerance
for that sort of problem now.”
The new editing procedures, which have been applied to the entire
German-language version of Wikipedia during the last year, are certain to be a
topic of discussion this week when Wikipedia’s volunteer editors gather in
Buenos Aires for their annual Wikimania conference. Much of the agenda is
focused on the implications of the encyclopedia’s size and influence.
Although Wikipedia has prevented anonymous users from creating new articles for
several years now, the new flagging system crosses a psychological Rubicon. It
will divide Wikipedia’s contributors into two classes — experienced, trusted
editors, and everyone else — altering Wikipedia’s implicit notion that everyone
has an equal right to edit entries.
That right was never absolute, and the policy changes are an extension of
earlier struggles between control and openness.
For example, certain popular or controversial pages, like the ones for the
singer Britney Spears and for President Obama, are frequently “protected” or
“semi-protected,” limiting who, if anyone, can edit the articles.
And for seven months beginning in November, The New York Times worked with
Wikipedia administrators to suppress information about the kidnapping of David
Rohde, a correspondent in Afghanistan, from the article about him. The Times
argued that the censorship would improve his chances of survival. Mr. Rohde
escaped from his Taliban captors in June, but the episode dismayed some
Wikipedia contributors.
The new system comes as some recent studies have found Wikipedia is no longer as
attractive to first-time or infrequent contributors as it once was.
Ed H. Chi of the Palo Alto Research Center in California, which specializes in
research for commercial endeavors, recently completed a study of the millions of
changes made to Wikipedia in a month. He concluded that the site’s growth
(whether in new articles, new edits or new contributors) hit a plateau in
2007-8.
For some active Wikipedia editors, this was an expected development — after so
many articles, naturally there are fewer topics to uncover, and those new topics
are not necessarily of general interest.
But Mr. Chi also found that the changes made by more experienced editors were
more likely to stay up on the site, whereas one-time editors had a much higher
chance of having their edits reversed. He concluded that there was “growing
resistance from the Wikipedia community to new content.”
To other observers, the new flagging system reflects Wikipedia’s necessary
acceptance of the responsibility that comes with its vast influence.
“Wikipedia now has the ability to alter the world that it attempts to document,”
said Joseph Reagle, an adjunct professor of communications at New York
University whose Ph.D. thesis was about the history of Wikipedia.
Under the current system, it is not difficult to insert false information into a
Wikipedia entry, at least for a short time. In March, for example, a 22-year-old
Irish student planted a false quotation attributed to the French composer
Maurice Jarre shortly after Mr. Jarre’s death. It was promptly included in
obituaries about Mr. Jarre in several newspapers, including The Guardian and The
Independent in Britain. And on Jan. 20, vandals changed the entries for two
ailing senators, Edward M. Kennedy and Robert C. Byrd, to report falsely that
they had died.
Flagged revisions, advocates say, could offer one more chance to catch such
hoaxes and improve the overall accuracy of Wikipedia’s entries.
Foundation officials intend to put the system into effect first with articles
about living people because those pieces are ripe for vandalism and because
malicious information within them can be devastating to those individuals.
Exactly who will have flagging privileges has not yet been determined, but the
editors will number in the thousands, Wikipedia officials say. With German
Wikipedia, nearly 7,500 people have the right to approve a change. The English
version, which has more than three times as many articles, would presumably need
even more editors to ensure that changes do not languish before approval.
“It is a test,” said Jimmy Wales, a founder of Wikipedia. “We will be interested
to see all the questions raised. How long will it take for something to be
approved? Will it take a couple of minutes, days, weeks?”
Mr. Wales began pushing for the policy after the Kennedy and Byrd hoaxes, but
discussions about a review system date back to one of the darkest episodes in
Wikipedia’s history, known as the Seigenthaler incident.
In 2005, the prominent author and journalist John Seigenthaler Sr. discovered
that Wikipedia’s biographical article connected him to the assassinations of
John F. Kennedy and Robert F. Kennedy, a particularly scurrilous thing to report
because he was personally close to the Kennedy family.
Since then, Wikipedians have been fanatical about providing sources for facts,
with teams of editors adding the label “citation needed” to any sentence without
a footnote.
“We have really become part of the infrastructure of how people get
information,” Mr. Wales said. “There is a serious responsibility we have.”
Wikipedia to Limit
Changes to Articles on People, NYT, 25.8.2009,
http://www.nytimes.com/2009/08/25/technology/internet/25wikipedia.html
Mining the Web for Feelings, Not Facts
August 24, 2009
The New York Times
By ALEX WRIGHT
Computers may be good at crunching numbers, but can they crunch feelings?
The rise of blogs and social networks has fueled a bull market in personal
opinion: reviews, ratings, recommendations and other forms of online expression.
For computer scientists, this fast-growing mountain of data is opening a
tantalizing window onto the collective consciousness of Internet users.
An emerging field known as sentiment analysis is taking shape around one of the
computer world’s unexplored frontiers: translating the vagaries of human emotion
into hard data.
This is more than just an interesting programming exercise. For many businesses,
online opinion has turned into a kind of virtual currency that can make or break
a product in the marketplace.
Yet many companies struggle to make sense of the caterwaul of complaints and
compliments that now swirl around their products online. As sentiment analysis
tools begin to take shape, they could not only help businesses improve their
bottom lines, but also eventually transform the experience of searching for
information online.
Several new sentiment analysis companies are trying to tap into the growing
business interest in what is being said online.
“Social media used to be this cute project for 25-year-old consultants,” said
Margaret Francis, vice president for product at Scout Labs in San Francisco.
Now, she said, top executives “are recognizing it as an incredibly rich vein of
market intelligence.”
Scout Labs, which is backed by the venture capital firm started by the CNet
founder Halsey Minor, recently introduced a subscription service that allows
customers to monitor blogs, news articles, online forums and social networking
sites for trends in opinions about products, services or topics in the news.
In early May, the ticket marketplace StubHub used Scout Labs’ monitoring tool to
identify a sudden surge of negative blog sentiment after rain delayed a
Yankees-Red Sox game.
Stadium officials mistakenly told hundreds of fans that the game had been
canceled, and StubHub denied fans’ requests for refunds, on the grounds that the
game had actually been played. But after spotting trouble brewing online, the
company offered discounts and credits to the affected fans. It is now
re-evaluating its bad weather policy.
“This is a canary in a coal mine for us,” said John Whelan, StubHub’s director
of customer service.
Jodange, based in Yonkers, offers a service geared toward online publishers that
lets them incorporate opinion data drawn from over 450,000 sources, including
mainstream news sources, blogs and Twitter.
Based on research by Claire Cardie, a former Cornell computer science professor,
and Jan Wiebe of the University of Pittsburgh, the service uses a sophisticated
algorithm that not only evaluates sentiments about particular topics, but also
identifies the most influential opinion holders.
Jodange, whose early investors include the National Science Foundation, is
currently working on a new algorithm that could use opinion data to predict
future developments, like forecasting the impact of newspaper editorials on a
company’s stock price.
In a similar vein, The Financial Times recently introduced Newssift, an
experimental program that tracks sentiments about business topics in the news,
coupled with a specialized search engine that allows users to organize their
queries by topic, organization, place, person and theme.
Using Newssift, a search for Wal-Mart reveals that recent sentiment about the
company is running positive by a ratio of slightly better than two to one. When
that search is refined with the suggested term “Labor Force and Unions,”
however, the ratio of positive to negative sentiments drops closer to one to
one.
Such tools could help companies pinpoint the effect of specific issues on
customer perceptions, helping them respond with appropriate marketing and public
relations strategies.
For casual Web surfers, simpler incarnations of sentiment analysis are sprouting
up in the form of lightweight tools like Tweetfeel, Twendz and Twitrratr. These
sites allow users to take the pulse of Twitter users about particular topics.
A quick search on Tweetfeel, for example, reveals that 77 percent of recent
tweeters liked the movie “Julie & Julia.” But the same search on Twitrratr
reveals a few misfires. The site assigned a negative score to a tweet reading
“julie and julia was truly delightful!!” That same message ended with “we all
felt very hungry afterwards” — and the system took the word “hungry” to indicate
a negative sentiment.
While the more advanced algorithms used by Scout Labs, Jodange and Newssift
employ advanced analytics to avoid such pitfalls, none of these services works
perfectly. “Our algorithm is about 70 to 80 percent accurate,” said Ms. Francis,
who added that its users can reclassify inaccurate results so the system learns
from its mistakes.
Translating the slippery stuff of human language into binary values will always
be an imperfect science, however. “Sentiments are very different from
conventional facts,” said Seth Grimes, the founder of the suburban Maryland
consulting firm Alta Plana, who points to the many cultural factors and
linguistic nuances that make it difficult to turn a string of written text into
a simple pro or con sentiment. “ ‘Sinful’ is a good thing when applied to
chocolate cake,” he said.
The simplest algorithms work by scanning keywords to categorize a statement as
positive or negative, based on a simple binary analysis (“love” is good, “hate”
is bad). But that approach fails to capture the subtleties that bring human
language to life: irony, sarcasm, slang and other idiomatic expressions.
Reliable sentiment analysis requires parsing many linguistic shades of gray.
“We are dealing with sentiment that can be expressed in subtle ways,” said Bo
Pang, a researcher at Yahoo who co-wrote “Opinion Mining and Sentiment
Analysis,” one of the first academic books on sentiment analysis.
To get at the true intent of a statement, Ms. Pang developed software that looks
at several different filters, including polarity (is the statement positive or
negative?), intensity (what is the degree of emotion being expressed?) and
subjectivity (how partial or impartial is the source?).
For example, a preponderance of adjectives often signals a high degree of
subjectivity, while noun- and verb-heavy statements tend toward a more neutral
point of view.
As sentiment analysis algorithms grow more sophisticated, they should begin to
yield more accurate results that may eventually point the way to more
sophisticated filtering mechanisms. They could become a part of everyday Web
use.
“I see sentiment analysis becoming a standard feature of search engines,” said
Mr. Grimes, who suggests that such algorithms could begin to influence both
general-purpose Web searching and more specialized searches in areas like
e-commerce, travel reservations and movie reviews.
Ms. Pang envisions a search engine that fine-tunes results for users based on
sentiment. For example, it might influence the ordering of search results for
certain kinds of queries like “best hotel in San Antonio.”
As search engines begin to incorporate more and more opinion data into their
results, the distinction between fact and opinion may start blurring to the
point where, as David Byrne once put it, “facts all come with points of view.”
Mining the Web for
Feelings, Not Facts, NYT, 24.8.2009,
http://www.nytimes.com/2009/08/24/technology/internet/24emotion.html
Ads Follow Web Users, and Get Much More Personal
July 31, 2009
The New York Times
By STEPHANIE CLIFFORD
For all the concern and uproar over online privacy, marketers and data
companies have always known much more about consumers’ offline lives, like
income, credit score, home ownership, even what car they drive and whether they
have a hunting license. Recently, some of these companies have started
connecting this mountain of information to consumers’ browsers.
The result is a sea change in the way consumers encounter the Web. Not only will
people see customized advertising, they will see different versions of Web sites
from other consumers and even receive different discount offers while shopping —
all based on information from their offline history. Two women in adjoining
offices could go to the same cosmetic site, but one might see a $300 Missoni
perfume, the other the house-brand lipstick on sale for $2.
The technology that makes the connection is nothing new — it is a tiny piece of
code called a cookie that is placed on a hard drive. But the information it
holds is. And it is all done invisibly.
“Now, you’re traveling the Internet with a cookie that indicates you’re this
type of consumer: age group X, income level, urban versus rural, presence of
children in the household,” said Trey Barrett, a product leader at Acxiom, one
of the companies offering this linking to marketers.
Advertisers and marketers say this specificity is useful, taking out the
guesswork involved in online-only profiling, and showing products to the people
most likely to be interested. Retailers including Gap and Victoria’s Secret are
using this tactic.
But consumer advocates say such unseen tracking is troubling. On the old
Internet, nobody knew you were a dog. On the new targeted Internet, they now
know what kind of dog you are, your favorite leash color, the last time you had
fleas and the date you were neutered.
“The industry’s love affair with persistent cookies has made it virtually
impossible for users to go online without being tracked and profiled,” said Marc
Rotenberg, executive director of the Electronic Privacy Information Center, in
an e-mail message.
While Congress has been holding hearings on online privacy lately, the sessions
have focused on online behavioral targeting. The industry has argued that no
government intervention is needed, an argument that the Federal Trade Commission
has so far accepted.
Consumers can avoid cookie-based tracking by deleting cookies from their
computers or setting their browsers not to accept cookies. But few do, and
privacy advocates say it is easy for companies to add cookies without users
noticing.
For decades, data companies like Experian and Acxiom have compiled reams of
information on every American: Acxiom estimates it has 1,500 pieces of data on
every American, based on information from warranty cards, bridal and birth
registries, magazine subscriptions, public records and even dog registrations
with the American Kennel Club.
Patrick Williams, the publisher of the personal finance magazine Worth, recently
asked Acxiom to find the names and addresses of 10,000 Americans from each of 11
cities who had houses worth more than $1 million, net worth of over $2 million,
lived within a few miles of other rich people and subscribed to business
publications.
“They are the scariest data research company around — they know far too much,”
said Mr. Williams, who said he was very happy with the amount of information it
gave him.
Companies like Acxiom and a competitor, Datran Media, make the connection
between online and offline data when a person registers on a Web site or clicks
through on an e-mail message from a marketer.
Datran’s cookies include 50 to 100 pieces of information. Both companies say
cookie data is anonymous and generalized. Datran and Acxiom then sell
advertising on Web sites like NBC.com, Facebook and Yahoo to companies that use
their data.
For marketers, all this data is a boon. Beltone New England, a hearing-aid
company, asked Datran to find people online who were 65 and over, owned a house,
were head of a household, made more than $35,000 a year and lived in New England
so it could show them ads. Datran also tested the same ads with a wider group of
people.
“What was surprising was we found the majority of responders turned out to be
women 35 to 40 who had elderly parents at home,” said Perry Ebel, Beltone’s
director of marketing and business development. He said he was changing his
offline marketing to include that group.
By using real-world data online, marketers can customize messages even further —
showing different products to people with different shopping habits, whether it
is in ads, an e-mail message or in semipersonalized Web pages.
Rodale, which publishes books along with magazines like Men’s Health and
Prevention, uses Acxiom data to help determine which promotional e-mails to send
to which customers. Offers aimed at women might be accompanied by an e-mail
message offering a Father’s Day subscription to Men’s Health for him and a free
book on losing belly fat for her. Young men might get another offer — a book on
sex positions. Some marketers are using offline data more subtly — for example,
showing a budget shopper a discount offer and a regular shopper a full-price
section.
“The people who buy less frequently and are most price-conscious may get a
better deal than someone who buys more frequently, who would buy anyway,” said
Christopher S. Marriott, global managing director of Acxiom Digital, a division
of Acxiom.
Of course, shoppers would have little reason to think their experience or their
ads are being personalized based on their home value or Volvo ownership.
“It is a little Big Brother-ish,” said Betsy Coggswell, 49, a social worker in
Fullerton, Calif., who shops online regularly. Still, she said, she wasn’t
shocked. “Every time you put out information about yourself — people have got to
understand — it’s going to be collected by somebody.”
Some online companies avoid matching online and offline profiles. In 2000,
DoubleClick abandoned plans to connect online and offline data after a huge
outcry. Google, which later acquired DoubleClick, has been conducting studies
that connect the two areas, but it does not currently collect or serve ads based
on such personal information without user permission, Sandra Heikkinen, a Google
spokeswoman, said.
While Acxiom, Datran and some of their partners address their use of tracking in
their privacy policies, such policies have become worthless, Mr. Rotenberg said.
“Real transparency means that the user gets access to the information, not to a
policy about the information,” he said.
Paul M. Schwartz, a law professor and privacy expert at the law school of the
University of California, Berkeley, said the unwitting participation by
consumers makes online marketing different from offline.
“Interactive media really gets into this creepy Orwellian thing, where it’s a
record of our thoughts on the way to decision-making,” he said. “We’re like the
data-input clerks now for the industry.”
Ads Follow Web Users,
and Get Much More Personal, NYT, 31.7.2009,
http://www.nytimes.com/2009/07/31/business/media/31privacy.html?hp
Op-Ed Contributor
Lost in the Cloud
July 20, 2009
The New York Times
By JONATHAN ZITTRAIN
Cambridge, Mass.
EARLIER this month Google announced a new operating system called Chrome. It’s
meant to transform personal computers and handheld devices into single-purpose
windows to the Web. This is part of a larger trend: Chrome moves us further away
from running code and storing our information on our own PCs toward doing
everything online — also known as in “the cloud” — using whatever device is at
hand.
Many people consider this development to be as sensible and inevitable as the
move from answering machines to voicemail. With your stuff in the cloud, it’s
not a catastrophe to lose your laptop, any more than losing your glasses would
permanently destroy your vision. In addition, as more and more of our
information is gathered from and shared with others — through Facebook, MySpace
or Twitter — having it all online can make a lot of sense.
The cloud, however, comes with real dangers.
Some are in plain view. If you entrust your data to others, they can let you
down or outright betray you. For example, if your favorite music is rented or
authorized from an online subscription service rather than freely in your
custody as a compact disc or an MP3 file on your hard drive, you can lose your
music if you fall behind on your payments — or if the vendor goes bankrupt or
loses interest in the service. Last week Amazon apparently conveyed a
publisher’s change-of-heart to owners of its Kindle e-book reader: some
purchasers of Orwell’s “1984” found it removed from their devices, with nothing
to show for their purchase other than a refund. (Orwell would be amused.)
Worse, data stored online has less privacy protection both in practice and under
the law. A hacker recently guessed the password to the personal e-mail account
of a Twitter employee, and was thus able to extract the employee’s Google
password. That in turn compromised a trove of Twitter’s corporate documents
stored too conveniently in the cloud. Before, the bad guys usually needed to get
their hands on people’s computers to see their secrets; in today’s cloud all you
need is a password.
Thanks in part to the Patriot Act, the federal government has been able to
demand some details of your online activities from service providers — and not
to tell you about it. There have been thousands of such requests lodged since
the law was passed, and the F.B.I.’s own audits have shown that there can be
plenty of overreach — perhaps wholly inadvertent — in requests like these.
The cloud can be even more dangerous abroad, as it makes it much easier for
authoritarian regimes to spy on their citizens. The Chinese government has used
the Chinese version of Skype instant messaging software to monitor text
conversations and block undesirable words and phrases. It and other
authoritarian regimes routinely monitor all Internet traffic — which, except for
e-commerce and banking transactions, is rarely encrypted against prying eyes.
With a little effort and political will, we could solve these problems.
Companies could be required under fair practices law to allow your data to be
released back to you with just a click so that you can erase your digital
footprints or simply take your business (and data) elsewhere. They could also be
held to the promises they make about content sold through the cloud: If they
sell you an e-book, they can’t take it back or make it less functional later. To
increase security, companies that keep their data in the cloud could adopt safer
Internet communications and password practices, including the use of biometrics
like fingerprints to validate identity.
And some governments can be persuaded — or perhaps required by their independent
judiciaries — to treat data entrusted to the cloud with the same level of
privacy protection as data held personally. The Supreme Court declared in 1961
that a police search of a rented house for a whiskey still was a violation of
the Fourth Amendment privacy rights of the tenant, even though the landlord had
given permission for the search. Information stored in the cloud deserves
similar safeguards.
But the most difficult challenge — both to grasp and to solve — of the cloud is
its effect on our freedom to innovate. The crucial legacy of the personal
computer is that anyone can write code for it and give or sell that code to you
— and the vendors of the PC and its operating system have no more to say about
it than your phone company does about which answering machine you decide to buy.
Microsoft might want you to run Word and Internet Explorer, but those had better
be good products or you’ll switch with a few mouse clicks to OpenOffice
orFirefox.
Promoting competition is only the tip of the iceberg — there are also the
thousands of applications so novel that they don’t yet compete with anything.
These tend to be produced by tinkerers and hackers. Instant messaging,
peer-to-peer file sharing and the Web itself all exist thanks to people out in
left field, often writing for fun rather than money, who are able to tempt the
rest of us to try out what they’ve done.
This freedom is at risk in the cloud, where the vendor of a platform has much
more control over whether and how to let others write new software. Facebook
allows outsiders to add functionality to the site but reserves the right to
change that policy at any time, to charge a fee for applications, or to
de-emphasize or eliminate apps that court controversy or that they simply don’t
like. The iPhone’s outside apps act much more as if they’re in the cloud than on
your phone: Apple can decide who gets to write code for your phone and which of
those offerings will be allowed to run. The company has used this power in ways
that Bill Gates never dreamed of when he was the king of Windows: Apple is
reported to have censored e-book apps that contain controversial content,
eliminated games with political overtones, and blocked uses for the phone that
compete with the company’s products.
The market is churning through these issues. Amazon is offering a generic
cloud-computing infrastructure so anyone can set up new software on a new Web
site without gatekeeping by the likes of Facebook. Google’s Android platform is
being used in a new generation of mobile phones with fewer restrictions on
outside code. But the dynamics here are complicated. When we vest our activities
and identities in one place in the cloud, it takes a lot of dissatisfaction for
us to move. And many software developers who once would have been writing
whatever they wanted for PCs are simply developing less adventurous, less
subversive, less game-changing code under the watchful eyes of Facebook and
Apple.
If the market settles into a handful of gated cloud communities whose
proprietors control the availability of new code, the time may come to ensure
that their platforms do not discriminate. Such a demand could take many forms,
from an outright regulatory requirement to a more subtle set of incentives — tax
breaks or liability relief — that nudge companies to maintain the kind of
openness that earlier allowed them a level playing field on which they could
lure users from competing, mighty incumbents.
We’ve only just begun to measure this problem, even as we fly directly into the
cloud. That’s not a reason to turn around. But we must make sure the cloud does
not hinder the creation of revolutionary software that, like the Web itself, can
seem esoteric at first but utterly necessary later.
Jonathan Zittrain, a law professor at Harvard, is the author of “The Future
of the Internet — And How to Stop It.”
Lost in the Cloud, NYT,
20.7.2009,
http://www.nytimes.com/2009/07/20/opinion/20zittrain.html
Cyberattacks Hit U.S. and South Korean Web Sites
July 9, 2009
The New York Times
By CHOE SANG-HUN
SEOUL, South Korea — Cyberattacks that have crippled the Web sites of several
major American and South Korean government agencies since the July 4th holiday
weekend appear to have been launched by a hostile group or government, South
Korea’s main government spy agency said on Wednesday.
Although the National Intelligence Service did not identify whom they believed
responsible, the South Korean news agency Yonhap reported that the spy agency
had implicated North Korea or pro-North Korea groups.
A spokesman at the intelligence agency said it could not confirm the Yonhap
report, which said that the spy agency briefed lawmakers about their suspicions
on Wednesday. The opposition Democratic Party accused the spy agency of
spreading unsubstantiated rumors to whip up support for a new anti-terrorism
bill that would give it more power.
Access to at least 11 major Web sites in South Korea — including those of the
presidential Blue House, the Defense Ministry, the National Assembly, Shinhan
Bank, the mass-circulation daily newspaper Chosun Ilbo and the top Internet
portal Naver.com — have crashed or slowed down to a crawl since Tuesday evening,
according to the government’s Korea Information Security Agency.
On Wednesday, some of the sites regained service, but others remained unstable
or inaccessible.
In an attack linked with the one in South Korea, 14 major Web sites in the
United States — including those of the White House, the State Department and the
New York Stock Exchange — came under similar attacks, according to
anti-cyberterrorism police officers in Seoul.
“This is not a simple attack by an individual hacker, but appears to be
thoroughly planned and executed by a specific organization or on a state level,”
the National Intelligence Service said in a statement, adding that it is
cooperating with the American investigative authorities to investigate the
attacks.
The Associated Press reported Tuesday night that a widespread and unusually
resilient computer attack that began July 4 knocked out the Web sites of several
American government agencies, including some that are responsible for fighting
cybercrime.
The Treasury Department, Secret Service, Federal Trade Commission and
Transportation Department Web sites were all down at varying points over the
holiday weekend and into this week, The A.P. reported, citing officials inside
and outside the American government. The fact that the government Web sites were
still being affected after three days signaled an unusually lengthy and
sophisticated attack, the news agency reported, citing anonymous American
officials.
The Washington Post, which also came under attack, reported on its Web site
Wednesday that a total of 26 Web sites were targeted. In addition to sites run
by government agencies, several commercial Web sites were also attacked,
including those operated by Nasdaq, it reported, citing researchers involved in
the investigation.
Amy Kudwa, a Department of Homeland Security spokeswoman, said that the agency
was aware of the attacks on “federal and private sector public-facing Web
sites.” The department, she said, has issued a notice to federal departments and
agencies, as well as other partner organizations, on the activity and advised
them of steps to take to help mitigate against such attacks.
“We see attacks on federal networks every day, and measures in place have
minimized the impact to federal websites,” she said.
In the attack, an army of thousands of “zombie computers” infected by the
hackers’ program were ordered to request access to these Web sites
simultaneously, causing an overload that caused the sites’ servers to crash,
South Korean officials said.
Although most of the North Korean military’s hardware is decrepit, the South
Korean authorities have recently voiced their concern over possible cyberattacks
from the North. In May, South Korean media reported that North Korea was running
a cyberwarfare unit that operates through the Chinese Internet network and tries
to hack into American and South Korean military networks.
In South Korea, the Blue House reported no data loss or other damage except
disrupted access. The Defense Ministry and banks attacked also reported no
immediate loss of security data or financial damage.
“The traffic to our site surged nine times of the normal level,” the Blue House
said in a statement. “Computer users in some regions still suffer slow or no
access at all to our site.”
Hwang Cheol-jeung, a senior official at the government’s Korea Communications
Commission, said the attacks were launched by computers infected by a well-known
“distributed denial of service,” or DDoS, hackers’ program.
The spy agency said 12,000 computers in South Korea and 8,000 overseas appeared
to have been mobilized in the attacks. The Korea Communications Commission
reported 22,000 infected computers.
“The infected computers are still attacking, and their number is not
decreasing,” Mr. Hwang told reporters in a briefing. The government was urging
users to upgrade their computers’ antivirus software.
Denial of service attacks against Web sites are not uncommon, but they can be
made far more serious if hackers infect and use thousands of computers. Hackers
frequently take aim at the American government: According to the Homeland
Security Department, there were 5,499 known breaches of American government
computers in 2008, up from 3,928 the previous year, and just 2,172 in 2006, The
A.P. said.
The South Korean news agency Yonhap said the police have traced a possible
starting point for the attack back to members of a small cable TV Web site in
Seoul. But officials said that does not mean it originated there.
Mr. Hwang said South Korean authorities suspected that the hackers used a new
variant of the denial of service program to attack the Web sites.
Sharon Otterman contributed reporting from New York.
Cyberattacks Hit U.S.
and South Korean Web Sites, NYT, 9.7.2009,
http://www.nytimes.com/2009/07/09/technology/09cyber.html
City Asks Applicants for Internet Passwords
June 19, 2009
Filed at 10:47 a.m. ET
By THE ASSOCIATED PRESS
The New York Times
HELENA, Mont. (AP) -- Job applicants with the city of Bozeman are finding
that their private Internet discussions and pictures may not be so private after
all.
The city is asking job seekers for the user names and passwords to Internet
social networking or Web groups they belong too. The decision is sparking an
outcry from those who say the policy goes way too far.
The issue has spawned hundreds of comments on Web forums and sharp criticism
from legislators and the ACLU.
''I liken it to them saying they want to look at your love letters and your
family photos,'' said Amy Cannata, with the American Civil Liberties Union of
Montana. ''I think this policy certainly crosses the privacy line.''
The city argues that it only uses the information to verify application
information -- and says it won't hold it against anyone for refusing to provide
it. City officials say such checks can be useful, especially when hiring police
officers and others in a position of public trust.
Bozeman officials have been hammered with e-mails and phone calls ever since
KBZK-TV of Bozeman reported the policy on Wednesday, including an excerpt from
the city application form that states ''Please list any and all current personal
or business Web sites, web pages or memberships on any Internet-based chat
rooms, social clubs or forums, to include, but not limited to: Facebook, Google,
Yahoo, YouTube.com, MySpace, etc.''
Bozeman City Commissioner Jeff Rupp said he was unaware city officers had
implemented the policy, and expects the city commission will be talking about
it. But Rupp said it is not as bad as it sounds since applicants are not scored
negatively for refusing to answer the question.
''I can tell you I would not provide it in an application I submit,'' Rupp said.
''I have been told repeatedly it is not scored, and the application is not
discarded if not provided.''
Rep. Brady Wiseman, a Bozeman Democrat, led the state's fight against the
Patriot Act when the Legislature issued a harsh critique of the federal act,
arguing it trampled civil liberties and put the government into a position of
snooping on citizens.
Wiseman said Bozeman now is going too far.
''Asking for passwords is over the line,'' Wiseman said. ''I think that this
notion opens up a whole new line of debate on privacy.''
The intense pressure generated in just a couple days is hitting the city hard.
Bozeman City Attorney Greg Sullivan told the Bozeman Daily Chronicle Thursday
that the city may look at changing the policy so that they could view an
applicant's social networking sites without asking for login information. One
option would be to have an applicant add the city as a ''friend'' on such sites
as Facebook.
''We've already began that discussion,'' Sullivan said.
Cannata, with the ACLU, said her organization has not found another government
body that asks for such information. And even though the ACLU has not done a
full legal analysis, she said the Bozeman policy doesn't pass the smell test.
''It's one thing, and I think totally reasonable, if someone has a public
profile to go check it out,'' Cannata said.
But private groups and profile could reveal information employers could not
legally base hiring decisions on, such as a person's religion, she added.
''Are they going to go in and look at those things?'' Cannata said. ''And even
if they don't intend to look at those things, it's still there for them to
see.''
City Asks Applicants for
Internet Passwords, NYT, 19.6.2009,
http://www.nytimes.com/aponline/2009/06/19/us/AP-US-Internet-Background-Checks.html
Keeping a True Identity Becomes a Battle Online
June 18, 2009
The New York Times
By BRAD STONE
SAN FRANCISCO — Since Facebook started giving out customized Web addresses
like facebook.com/yourname last Friday, some 9.5 million people have rushed to
grab their top choice.
On Twitter, public fights have broken out over so-called impostor accounts, like
those that should probably be in the hands of Kanye West or Bank of America.
And somewhere out there on the Web, another new service or social network is on
the rise, threatening to start yet another online land grab.
Celebrities, companies and even regular people can be excused for feeling a bit
of déjà vu. Staking out and protecting their names and trademarks on the
Internet has become a seemingly never-ending battle. With the rise of social
networks, registering a simple Web address like pepsi.com or mileycyrus .com is
no longer enough to plant one’s flag firmly in the virtual terra firma.
When domain names first became hot properties in the ’90s, it was mostly
companies that worried about claiming the right addresses. But in this more
narcissistic Internet era, people who were once happily anonymous view
themselves as online minicelebrities with their own brands to promote.
Those whose names are not unique may run into problems in trying to manage those
brands. Chris Hardwick, a stand-up comedian and host on the tech-focused cable
network G4, had no trouble registering chrishardwick.com a few years ago and
securing the appropriate Gmail address. But he missed out on claiming his name
on MySpace to a Chris Hardwick in Ohio. Last weekend, Mr. Hardwick got home from
a performance too late to get his address of choice on Facebook; he said a high
school student in England appeared to have grabbed it.
“It’s like a Wild West town full of Chris Hardwicks with their hands on their
mouses getting ready to draw on each other,” he said.
To some, the rules of this new game are frustratingly hazy. Facebook has invited
trademark holders and celebrities who find their names are taken to fill out a
complaint form on the site. It says it will resolve disputes on a case-by-case
basis. While Facebook’s social network has room for many people with the same
name, the new vanity addresses are being distributed on a
first-come-first-served basis.
Twitter has begun verifying the identities of well-known users, giving them a
badge on their pages that serves to confirm that they are who they say they are.
But it has revealed little about how that process works. A Twitter spokeswoman,
Jenna Sampson, said the program was a small-scale test at this point.
Tony LaRussa, manager of the St. Louis Cardinals baseball team, recently sued
Twitter, saying it did not do enough to prevent someone from tweeting under his
name. Twitter has called the lawsuit “frivolous” and says the network shuts down
accounts used by known impersonators.
Another problem is that no one knows whether any of this online terrain has any
lasting value — only that accounts on sites like Twitter and Facebook tend to
show up at the top of the list when people search the Web. So many people are
plunging in — including so-called cybersquatters who hope to profit, financially
or otherwise, from Web addresses and accounts.
Larry Winget, the author of four popular books on personal finance, has been
quick over the years to get control of his name on the Web and on sites like
MySpace. But last weekend, a professed fan beat him to facebook.com/larrywinget
and then said he would turn it over in exchange for a face-to-face dinner.
“It’s this constant effort, this sprint, to stay ahead of the technology,” Mr.
Winget said. “You’ve got to hire a person just to stay on top of it.”
Companies are feeling just as much anxiety over the online name game. RCN, a
cable and telephone service based in Herndon, Va., submitted a request last week
to Facebook to secure facebook.com/rcn. But then Facebook said companies would
need to have more than 1,000 fans on their pages to be eligible for the custom
address program. RCN’s recently created page had 527 fans as of Wednesday.
RCN executives say they are frustrated with Facebook’s rules and are worried
that they could lose what they suspect could be valuable real estate. Possible
competitors for the address include people and organizations with those
initials, along with the dreaded squatters.
“This is a new world that we are having to step into in order to protect our
brand, and they did not give us a huge window of time to prepare for it,” said
Ashlie Ellison, a Web producer for RCN.
Social media sites give companies new ways to promote their brands, said Howard
H. Weller, a trademark lawyer at Mitchell Silberberg & Knupp in New York. But he
added that “these are all new avenues for abuse, and it’s more resources
trademark owners need to devote to policing and enforcement.”
The Facebook Web addresses in particular could be worth nothing — Facebook has
said they will not be transferable, although users could quietly hand over the
passwords to their accounts.
But digital squatters are still trying, creating potential headaches for
companies. For example, Dell grabbed facebook.com/dell, but Jeremy Fancher, a
student at Washington University in St. Louis, registered
facebook.com/dellcomputer and plans to try to sell it. A Dell spokesman declined
to comment.
“I think it would be sort of funny if another computer company buys it,” Mr.
Fancher said. “It all illustrates how murky the water is when signing up for
these accounts.”
Keeping a True Identity
Becomes a Battle Online, NYT, 18.6.2009,
http://www.nytimes.com/2009/06/18/technology/internet/18name.html?hp
On Web and iPhone, a Tool to Aid Careful Shopping
June 15, 2009
The New York Times
By CLAIRE CAIN MILLER
SAN FRANCISCO — These days, every skin lotion and dish detergent on store
shelves gloats about how green it is. How do shoppers know which are good for
them and good for the earth?
It was a similar question that hit Dara O’Rourke, a professor of environmental
and labor policy at the University of California, Berkeley, one morning when he
was applying sunscreen to his young daughter’s face.
He realized he did not know what was in the lotion. He went to his office and
quickly discovered that it contained a carcinogen activated by sunlight. It also
contained an endocrine disruptor and two skin irritants. He also discovered that
her soap included a kind of dioxane, a carcinogen, and then found that one of
her brand-name toys was made with lead.
And in looking for the answer, he hatched the idea for a company that used his
esoteric research on supply chain management. “All I do is study this, and I
know nothing about the products I’m bringing into our house and putting in, on
and around our family,” Mr. O’Rourke said. But when he wanted to find that
information, he could. Most consumers would struggle to do so.
Hence GoodGuide, a Web site and iPhone application that lets consumers dig past
the package’s marketing spiel by entering a product’s name and discovering its
health, environmental and social impacts.
“What we’re trying to do is flip the whole marketing world on its head,” said
Mr. O’Rourke. “Instead of companies telling you what to believe, customers are
making the statements to the marketers about what they care about.”
A few years ago, Mr. O’Rourke noticed that at the end of his lectures, audience
members were raising their hands to ask which kind of laptop or sneaker or
lotion to buy. Americans are becoming increasingly interested in what is in the
stuff they buy. (Mr. O’Rourke’s research caught mainstream interest once before
when, in 1997, his report on Nike’s factories in Vietnam led to an uproar over
that company’s labor conditions.)
Although the GoodGuide Web site, which started in September, had only 110,000
unique visitors in April, Mr. O’Rourke is encouraged that it is growing about 25
percent a month. Lately, interest in GoodGuide has begun to extend beyond
techies and the Whole Foods crowd to the Wal-Mart crowd, as Mr. O’Rourke put it.
One sign of that broader appeal: Apple recently featured the app in its iPhone
ads.
GoodGuide’s office, in San Francisco, has 12 full-time and 12 part-time
employees, half scientists and half engineers. They have scored 75,000 products
with data from nearly 200 sources, including government databases, studies by
nonprofits and academics, and the research by scientists on the GoodGuide staff.
There are still holes in the data that GoodGuide seeks to fill.
Users enter a product’s name to get scores. For instance, Tom’s of Maine
deodorant gets an 8.6 in part because it has no carcinogens, while Arrid XX
antiperspirant rates a 3.8 because it contains known carcinogens. Another click
leads to information behind the scores, like whether an ingredient causes
reproductive problems or produces toxic waste, or whether the company has women
and racial minorities in executive positions or faces labor lawsuits.
Mr. O’Rourke began gathering data in 2005 with the help of computer science
graduate students at Berkeley and $300,000 from foundations. The do-gooder in
Mr. O’Rourke, however, did not prevent him from seeing the commercial
possibilities of what was being compiled.
Persuading venture capitalists to finance his idea was trickier. In 2007, he was
rejected by dozens of firms over six months. The green tech investors were not
interested in a start-up that did not make alternative energy. The Web investors
were not interested in one that was not going to get 50 million users overnight
and sell ads.
One of the most prominent Internet investors in Silicon Valley walked out of the
room after snidely dismissing GoodGuide with: “Hmm, a noble cause.” GoodGuide
eventually raised $3.7 million from New Enterprise Associates and Draper Fisher
Jurvetson.
GoodGuide does not sell ads and does not plan to, in part because Mr. O’Rourke
will not take money from a company whose product is rated on the site. It makes
a small fee if customers click on links to Amazon.com or TheFind and buy the
product.
The basic site will always be free, he says, but GoodGuide may someday charge
subscription fees for personalized versions. It also plans to license data to
governments and retailers. It could help a state avoid buying paper cups with
ingredients from a certain country, for example, or enable a drugstore chain to
list a product’s GoodGuide score next to the price tag.
This summer, GoodGuide will add a deeper database for users who want more detail
by, for example, reading the academic studies on which ratings may be based. The
next version of the iPhone will enable people to scan bar codes to get scores,
rather than type in the product’s name.
Some companies, including Clorox and SC Johnson, have agreed in recent months to
reveal more about the ingredients in their products because of gathering
consumer concern. That will enable GoodGuide to fill gaps in its data. Federal
law does not require makers of household products to list all ingredients.
“What we think of now as green is a marketing mirage,” usually based on a single
environmentally friendly practice, said Daniel Goleman, author of “Ecological
Intelligence,” who switched deodorants and shampoos because of GoodGuide. The
site could potentially “have a revolutionary effect on industry and commerce,”
he said, by educating shoppers about the ramifications of buying a particular
product.
That could also be the problem with GoodGuide, said John R. Ehrenfeld, executive
director of the International Society for Industrial Ecology. He worries that by
collapsing dozens of data points into a single number, GoodGuide does not
adequately inform consumers about each consequence of each ingredient.
“Consumers need to be very carefully educated as to what these scores mean if
it’s going to serve the purpose GoodGuide says it does,” he said.
On Web and iPhone, a
Tool to Aid Careful Shopping, NYT, 15.6.2009,
http://www.nytimes.com/2009/06/15/technology/internet/15guide.html?hpw
AP: Weak Security Opens Door to Credit Card Hacks
June 15, 2009
Filed at 11:11 a.m. ET
By THE ASSOCIATED PRESS
The New York Times
Every time you swipe your credit card and wait for the transaction to be
approved, sensitive data including your name and account number are ferried from
store to bank through computer networks, each step a potential opening for
hackers.
And while you may take steps to protect yourself against identity theft, an
Associated Press investigation has found the banks and other companies that
handle your information are not being nearly as cautious as they could.
The government leaves it to card companies to design security rules that protect
the nation's 50 billion annual transactions. Yet an examination of those
industry requirements explains why so many breaches occur: The rules are cursory
at best and all but meaningless at worst, according to the AP's analysis of data
breaches dating to 2005.
It means every time you pay with plastic, companies are gambling with your
personal data. If hackers intercept your numbers, you'll spend weeks
straightening your mangled credit, though you can't be held liable for
unauthorized charges. Even if your transaction isn't hacked, you still lose:
Merchants pass to all their customers the costs they incur from fraud.
More than 70 retailers and payment processors have disclosed breaches since
2006, involving tens of millions of credit and debit card numbers, according to
the Privacy Rights Clearinghouse. Meanwhile, many others likely have been
breached and didn't detect it. Even the companies that had the payment
industry's top rating for computer security, a seal of approval known as PCI
compliance, have fallen victim to huge heists.
Companies that are not compliant with the PCI standards -- including one in 10
of the medium-sized and large retailers in the United States -- face fines but
are left free to process credit and debit card payments. Most retailers don't
have to endure security audits, but can evaluate themselves.
Credit card providers don't appear to be in a rush to tighten the rules. They
see fraud as a cost of doing business and say stricter security would throw sand
into the gears of the payment system, which is built on speed, convenience and
low cost.
That is of little consolation to consumers who bet on the industry's payment
security and lost.
It took four months for Pamela LaMotte, 46, of Colchester, Vt., to fix the
damage after two of her credit card accounts were tapped by hackers in a breach
traced to a Hannaford Bros. grocery store.
LaMotte, who was unemployed at the time, says she had to borrow money from her
mother and boyfriend to pay $500 in overdraft and late fees -- which were
eventually refunded -- while the banks investigated.
''Maybe somebody who doesn't live paycheck to paycheck, it wouldn't matter to
them too much, but for me it screwed me up in a major way,'' she said. LaMotte
says she pays more by cash and check now.
It all happened at a supermarket chain that met the PCI standards. Someone
installed malicious software on Hannaford's servers that snatched customer data
while it was being sent to the banks for approval.
Since then, hackers plundered two companies that process payments and had PCI
certification. Heartland Payment Systems lost card numbers, expiration dates and
other data for potentially hundreds of millions of shoppers. RBS WorldPay Inc.
got taken for more than 1 million Social Security numbers -- a golden ticket to
hackers that enables all kinds of fraud.
In the past, each credit card company had its own security rules, a system that
was chaotic for stores.
In 2006, the big card brands -- Visa, MasterCard, American Express, Discover and
JCB International -- formed the Payment Card Industry Security Standards Council
and created uniform security rules for merchants.
Avivah Litan, a Gartner Inc. analyst, says retailers and payment processors have
spent more than $2 billion on security upgrades to comply with PCI. And the
payment industry touts the fact that 93 percent of big retailers in the U.S.,
and 88 percent of medium-sized ones, are compliant with the PCI rules.
That leaves plenty of merchants out, of course, but the main threat against them
is a fine: $25,000 for big retailers for each month they are not compliant,
$5,000 for medium-sized ones.
Computer security experts say the PCI guidelines are superficial, including
requirements that stores run antivirus software and install computer firewalls.
Those steps are designed to keep hackers out and customer data in. Yet tests
that simulate hacker attacks are required just once a year, and businesses can
run the tests themselves.
''It's like going to a doctor and getting your blood pressure read, and if your
blood pressure's good you get a clean bill of health,'' said Tom Kellermann, a
former senior member of the World Bank's Treasury security team and now vice
president of security awareness for Core Security Technologies, which audited
Google's Internet payment processing system.
Merchants that decide to hire an outside auditor to check for compliance with
the PCI rules need not spend much. Though some firms generally charge about
$60,000 and take months to complete their inspections, others are far cheaper
and faster.
''PCI compliance can cost just a couple hundred bucks,'' said Jeremiah Grossman,
founder of WhiteHat Security Inc., a Web security firm. ''If that's the case,
all the incentives are in the wrong direction. The merchants are inclined to go
with the cheapest certification they need.''
For some inspectors, the certification course takes just one weekend and ends in
an open-book exam. Applicants must have five years of computer security
experience, but once they are let loose, there's little oversight of their work.
Larger stores take it on themselves to provide evidence to auditors that they
comply with the rules, leaving the door open for mistakes or fraud.
And retailers with fewer than 6 million annual card transactions -- a group
comprising more than 99 percent of all retailers -- do not even need auditors.
They can test and evaluate themselves.
At the same time, the card companies themselves are increasingly hands-off.
Two years ago, Visa scaled back its review of inspection records for the payment
processors it works with. It now examines records only for payment processors
with computer networks directly connected to Visa's.
In the U.S., that means fewer than 100 payment processors out of the 700 that
Visa works with are PCI-compliant.
Visa's head of global data security, Eduardo Perez, said the company scaled back
its records review because it took too much work and because the PCI standards
have improved the industry's security ''considerably.''
''I think we've made a lot of progress,'' he said. ''While there have been a few
large compromises, there are many more compromises we feel we've helped prevent
by driving these minimum requirements.''
Representatives for MasterCard, American Express, Discover and JCB -- which,
along with Visa, steer PCI policy -- either didn't return messages from the AP
or directed questions to the PCI security council.
PCI's general manager, Bob Russo, said inspector certification is ''rigorous.''
Yet he also acknowledged that inconsistent audits are a problem -- and that
merchants and payment processors who suffered data breaches possibly shouldn't
have been PCI-certified. Those companies also might have easily fallen out of
compliance after their inspection, by not installing the proper security
updates, and nobody noticed.
The council is trying to crack down on shoddy work by requiring annual audits
for the dozen companies that do the bulk of the PCI inspections. Smaller firms
will be examined once every three years.
Those reviews merely scratch the surface, though. Only three full-time staffers
are assigned to the task, and they can't visit retailers themselves. They are
left to review the paperwork from the examinations.
The AP contacted eight of the biggest ''acquiring banks'' -- the banks that
retailers use as middlemen between the stores and consumers' banks. Those banks
are responsible for ensuring that retailers are PCI compliant. Most didn't
return calls or wouldn't comment for this story.
Mike Herman, compliance managing director for Chase Paymentech, a division of
JPMorgan Chase, said his bank has five workers reviewing compliance reports from
retailers. Most of the work is done by phone or e-mail.
''We have faith in the certification process, and we really haven't doubted the
assessors' work,'' Herman said. ''It's really the merchants that don't engage
assessors; those get a little more scrutiny.''
He defended the system: ''Can you imagine how many breaches we'd have and how
severe they'd be if we didn't have PCI?''
Supporters of PCI point out nearly all big and medium-sized retailers governed
by the standard now say they no longer store sensitive cardholder data. Just a
few years ago they did -- leaving credit card numbers in databases that were
vulnerable to hackers.
So why are breaches still happening? Because criminals have sharpened their
attacks and are now capturing more data as it makes its way from store to bank,
when breaches are harder to stop.
Security experts say there are several steps the payment industry could take to
make sure customer information doesn't leak out of networks.
Banks could scramble the data that travels over payment networks, so it would be
meaningless to anyone not authorized to see it.
For example, TJX Cos., the chain that owns T.J. Maxx and Marshalls and was
victimized by a breach that exposed as many as 100 million accounts, the most on
record, has tightened its security but says many banks won't accept data in
encrypted form.
PCI requires data transmitted across ''open, public networks'' to be encrypted,
but that means hackers with access to a company's internal network still can get
at it. Requiring encryption all the time would be expensive and slow
transactions.
Another possibility: Some security professionals think the banks and credit card
companies should start their own PCI inspection arms to make sure the audits are
done properly. Banks say they have stepped up oversight of the inspections,
doing their own checks of questionable PCI assessment jobs. But taking control
of the whole process is far-fetched: nobody wants the liability.
PCI could also be optional. In its place, some experts suggest setting fines for
each piece of sensitive data a retailer loses.
The U.S. might also try a system like Europe's, where shoppers need a secret PIN
code and card with a chip inside to complete purchases. The system, called Chip
and PIN, has cut down on fraud there (because it's harder to use counterfeit
cards), but transferred it elsewhere -- to places like the U.S. that don't have
as many safeguards.
A key reason PCI exists is that the banks and card brands don't want the
government regulating credit card security. These companies also want to be sure
transactions keep humming through the system -- which is why banks and card
companies are willing to put up with some fraud.
''If they did mind, they have immense resources and could really change
things,'' said Ed Skoudis, co-founder of security consultancy InGuardians Inc.
and an instructor with the SANS Institute, a computer-security training
organization. Skoudis investigates retail breaches in support of government
investigations. ''But they don't want to strangle the goose that laid the golden
egg by making it too hard to accept credit cards, because that's bad for
everybody.''
AP: Weak Security Opens
Door to Credit Card Hacks, NYT, 15.6.2009,
http://www.nytimes.com/aponline/2009/06/15/business/AP-US-TEC-Shoppers-Gamble.html
Providing Cellphones for the Poor
June 15, 2009
The New York Times
By MATT RICHTEL
John Cobb, 59, a former commercial fisherman who is disabled with cirrhosis
of the liver and emphysema, lives in a studio apartment in Greensboro, N.C., on
a fixed monthly income of $674. He has been hoping to receive more government
assistance, and in February, he did.
It came in the form of a free cellphone and free service.
Mr. Cobb became one of a small but rapidly growing number of low-income
Americans benefiting from a new wrinkle to a decades-old federal law that
provided them with subsidized landline telephone service.
In a twist, wireless carriers are receiving subsidies to provide people like Mr.
Cobb with a phone and typically 68 minutes of talk time each month. It is a form
of wireless welfare that puts a societal stamp on the central role played by the
mobile device.
Mr. Cobb’s cellphone is a Motorola 175. “I feel so much safer when I drive. If I
get sick, I can call someone. If I break down, I can call someone,” Mr. Cobb
said. “It’s a necessity.”
The users are not the only ones receiving government assistance.
Telecommunications industry analysts said the program, while in its infancy,
could benefit mobile phone carriers, who face a steep challenge of their own:
most Americans already own a cellphone, so the poor represent a last untapped
market.
“The low hanging fruit is gone, and the wireless companies are going after the
nooks and crannies,” said Roger Entner, a wireless industry analyst with
Nielsen. “Oh, the poor: How can we sign them up?”
Carriers can receive up to $10 a month in government subsidies, sufficient to
cover what amounts to about $3 in service, Mr. Entner said.
Since November, the number of customers receiving free or subsidized wireless
service has doubled to 1.4 million, he said. To be eligible for the program,
known as Lifeline, a person must meet federal low-income guidelines or qualify
for one of a handful of social service programs, including food stamps or
Medicaid.
The opportunity has prompted interest from the nation’s biggest carriers,
including Sprint Nextel and AT&T. But at the forefront is a much smaller
company, Tracfone, a Florida provider of prepaid mobile service that has become
the face of the fledgling subsidized cellphone.
Tracfone began providing its service, called SafeLink, in Tennessee in August
and now does so in 16 states, including New York, North Carolina and
Pennsylvania, and the District of Columbia, according to its Web site. Each time
it enters a market — which generally requires state approval — it runs
television ads telling people how easy it is to get a free Motorola phone, like
Mr. Cobb’s.
The company says the economy makes the audience particularly receptive. “We’ll
read that more people are signing up for food stamps and look at our numbers and
see volume rising,” said Jose Fuentes, director of government relations for
Tracfone. “It’s not scientific proof,” he added. “But we know times are tough.”
He declined to say how many subscribers have signed up. But he said Tracfone,
whose paid service has 10 million subscribers, sees the Lifeline service as an
opportunity to make some money but, more pointedly, to eventually convert the
subsidized customers into paying ones if their fortunes turn around and they no
longer qualify for a free phone.
“It could make for a good business,” Mr. Fuentes said.
According to Nielsen, 90 percent of Americans have at least one cellphone. That
leaves 32 million, including the infirm, still up for grabs. “And the race is on
to get them,” Mr. Entner said.
He said the overwhelming majority of Americans with subsidized wireless service
receive it through Tracfone.
One of them is Leon Simmons, 52, of the Bronx, N.Y., who did stints in the Navy,
at the Post Office and as a security guard before becoming disabled with
emphysema. His wife, who works a minimum wage job at a laundry, heard about the
Tracfone service and he got a phone in April.
The free phone is not, as it is for some others in the program, their sole form
of telecommunications. Out of the roughly $1,600 they make each month after
taxes, they pay $159 for a landline telephone, high-speed Internet and cable
television. But the cellphone, Mr. Simmons says, gives him the flexibility to
tell his wife or daughter his comings and goings or to stay in touch when he is
at the doctor.
According to the Federal Communications Commission, Lifeline service was started
in 1984 to ensure that everyone had telephone service for emergencies. The
Telecommunications Act of 1996 opened competition to new wireline and wireless
providers.
More recently, companies, particularly Tracfone, have started pursuing the
wireless opportunity. Still, most of the $800 million in subsidies last year
went for landline service even as more Americans cut the cord in favor of
exclusively using a mobile phone.
The subsidy money comes from a tax applied to phone bills. Carriers seeking
eligibility for it apply to state utility commissions, though several states
have ceded their jurisdiction in the matter to the F.C.C.
The issue has created controversy in some states over how and even whether to
subsidize wireless service. In California, for example, the public utilities
commission plans to debate on Thursday a proposal to extend Lifeline services to
wireless — a matter backed by companies like AT&T and Sprint and T-Mobile.
The Greenlining Coalition, a nonprofit advocacy group for low-income residents,
has lobbied the state to “move the California Lifeline program into the 21st
century,” according to public documents provided for the hearing on Thursday.
But State Assemblyman Felipe Fuentes, who represents a district in Los Angeles,
says the California legislature should ask some tough questions before moving
ahead — particularly if people contemplate making wireless their only form of
communication. Chiefly, he wants to know whether wireless service satisfies
crucial aspects needed in lifeline, like reliability in an emergency.
“What if the phone isn’t charged, or junior doesn’t know how to use it?” Mr.
Fuentes asked.
Across the country, Mr. Simmons from the Bronx says he likes being able to
communicate when he is on the go. And he does not see what all the fuss is about
when it comes to cellphones.
“People walk around with their head stuck into these things, not paying
attention to what’s going on around them,” he said. Even though he thinks these
people look silly, he said, he is going to use his cellphone.
Why not? he said. “It’s free.”
Providing Cellphones for
the Poor, NYT, 15.6.2009,
http://www.nytimes.com/2009/06/15/technology/15cell.html?hp
Online, ‘a Reason to Keep on Going’
June 2, 2009
The New York Times
By STEPHANIE CLIFFORD
Like many older people, Paula Rice of Island City, Ky., has grown isolated in
recent years. Her four grown children live in other states, her two marriages
ended in divorce, and her friends are scattered. Most days, she does not see
another person.
But Ms. Rice, 73, is far from lonely. Housebound after suffering a heart attack
two years ago, she began visiting the social networking sites Eons.com, an
online community for aging baby boomers, and PoliceLink.com (she is a former
police dispatcher). Now she spends up to 14 hours a day in online conversations.
“I was dying of boredom,” she said. “Eons, all by its lonesome, gave me a reason
to keep on going.”
That more and more people in Ms. Rice’s generation are joining networks like
Eons, Facebook and MySpace is hardly news. Among older people who went online
last year, the number visiting social networks grew almost twice as fast as the
overall rate of Internet use among that group, according to the media
measurement company comScore. But now researchers who focus on aging are
studying the phenomenon to see whether the networks can provide some of the
benefits of a group of friends, while being much easier to assemble and
maintain.
“One of the greatest challenges or losses that we face as older adults, frankly,
is not about our health, but it’s actually about our social network
deteriorating on us, because our friends get sick, our spouse passes away,
friends pass away, or we move,” said Joseph F. Coughlin, director of the AgeLab
at the Massachusetts Institute of Technology.
“The new future of old age is about staying in society, staying in the workplace
and staying very connected,” he added. “And technology is going to be a very big
part of that, because the new reality is, increasingly, a virtual reality. It
provides a way to make new connections, new friends and new senses of purpose.”
About one-third of people 75 and older live alone, according to a 2009 study
from AARP. In response to the growing number of older Americans, the National
Institute on Aging is awarding at least $10 million in grants for researchers
who examine social neuroscience and its effect on aging.
Online networks may offer older people “a place where they do feel empowered,
because they can make these connections and they can talk to people without
having to ask a friend or a family member for one more thing,” said Antonina
Bambina, a sociologist at the University of Southern Indiana who wrote the book
“Online Social Support” (Cambria, 2007).
For the family members of older people, online social networks can provide a bit
of relief. Chris McWade of Franklin, Mass., the youngest member of a big family,
recently helped his parents, his grandparents and his uncle move to retirement
homes. He said he spent two or three years “just flying cross-country, holding a
lot of hands” and seeing the isolation and depression that came with aging.
That sparked the idea for MyWay Village, a social network based in Quincy, Mass.
Mr. McWade helped found it in 2006 and now sells it to retirement homes. It has
just completed pilot programs in several nursing homes in Illinois and
Massachusetts, and Mr. McWade says he has agreements to expand to several other
homes.
Two and a half years ago, Howe Allen, a real estate broker in Boston, moved his
parents to the River Bay Club, a retirement home in Quincy, Mass., that uses
MyWay.
His mother died soon after, but his father, Carl, was able to start making
friends and share stories on MyWay. The older man had never used a computer, but
picked it up quickly; the software includes computer training sessions. And
after he died last December, a memorial service at the home included photographs
he had uploaded to MyWay, excerpts from memoirs he had posted and eulogies from
friends he had made through the site.
“It was as moving a day as I can ever remember,” Howe Allen said. “It’s more
than just the computer. It affected him in ways that are so far from the
electronic age. It allowed this person to grow at an age where you assume most
people stop growing.”
On a recent Monday, Neil Sullivan, a regional manager for MyWay, stood in front
of a group of about 20 River Bay Club residents in the home’s library.
He came prepared with slides and speeches, but mostly the group just wanted to
talk about their lives. When Mr. Sullivan showed a photograph of a 1950
Chevrolet, one resident said, “I had a ’57 Chevy,” and another responded, “Mine
was a ’49 Chevy.” A man in a chartreuse sweater who had been quiet for some time
added, “The best car I ever had was a Dodge Business Coupe.”
Sarah Hoit, a co-founder of MyWay and its chief executive, said that for older
people, learning to get online was not an end in itself. “They want a vehicle to
meet new people and share their lives,” she said. “They want to be stimulated.”
Outside of the weekly sessions, River Bay residents use the site to post stories
like “My Life as a Nurse” or “I Worked at the Howard Johnson in Quincy.” Sunny
Walker, 89, who refused to use an electric typewriter when she was a school
secretary because she hated technology so much, now plays games and sends
friends messages through the site.
“I’m telling you, it’s the best thing for seniors,” she said. “It challenges
their mind, that’s what it does. It challenged mine.”
Some research suggests that loneliness can hasten dementia, and Dr. Nicholas A.
Christakis, an internist and social scientist at Harvard, says he is considering
research on whether online social connections can help delay dementia, as
traditional ones have been found to do in some studies.
“Online social networks realize an ancient propensity we all have to connect
with others,” he said.
The propensity may be ancient, but the means are not. Mollie Bourne, a golf
course owner who lives in Puerto Vallarta, Mexico, half of the year, logs on to
Facebook a few times a week. She likes to browse through her grandchildren’s
posts and photos, even the ones taken at bars and parties that are hardly the
sort that people expect their grandmothers to see.
“For heaven’s sakes, we all acted like that in college,” she said. “That’s one
thing you get with your 76 years. I’ve been around. I’ve seen it all. It takes a
lot to shock me.”
Online, ‘a Reason to
Keep on Going’, NYT, 2.6.2009,
http://www.nytimes.com/2009/06/02/health/02face.html?hpw
Microsoft Reveals New Strategy for Xbox
June 2, 2009
The New York Times
By SETH SCHIESEL
LOS ANGELES — Reaching out beyond hardcore video game players to everyday
consumers, Microsoft outlined an entertainment strategy on Monday for making the
company’s Xbox 360 game console a gateway for movies, television and social
networking.
In a media presentation on the eve of E3, the video game industry’s biggest
North American convention, Microsoft announced new relationships with the social
networking giants Facebook and Twitter as well as Sky, the big British satellite
television provider that is a unit of the News Corporation.
Microsoft announced that Facebook users would be able to access their profiles
and share photos on their television through the Xbox Live network and that
Twitter devotees would also be able to post and read messages through the
service.
More far-reaching was Microsoft’s new deal with Sky, under which Xbox Live users
in Britain will be able to watch live television, including professional soccer,
over an Internet version of the Sky service. Not every channel available over
satellite will be available over Xbox Live, but the offering will include dozens
of stations, Microsoft executives said. Users will be able to watch television
in a virtual party room with their friends, discussing the program as they are
watching, they said.
Microsoft executives refused to comment on whether the company was trying to
negotiate a similar deal with Sky’s sister satellite television operation in the
United States, DirecTV.
Microsoft has long sought a bigger role in home television, going so far in
years past as to try to build its own set-top box business. Partnering with Sky
represents a back door into the television market. The company has also
recognized how Nintendo has expanded the traditional audience for video games
with its innovative motion-sensitive controller for the Wii. Microsoft provided
the first public demonstration of its futuristic Project Natal, which it hopes
will usher in an age of completely controller-free gaming.
Using a sophisticated camera, infrared sensors and voice recognition software,
Natal allows users to control a game or other programs, like a virtual painting
studio, merely by waving their arms, speaking to the system and moving around.
Microsoft did not say when the technology would become available.
Microsoft also demonstrated some of its coming big games, including Forza
Motorsport 3, the suspense-thriller Alan Wake and a new version of its biggest
hit, Halo. Hideo Kojima, the developer behind the Metal Gear series, said that
the next major installment in that franchise would be available for Xbox 360, a
coup for Microsoft because previous Metal Gear games had been exclusive to Sony
game machines.
Microsoft Reveals New
Strategy for Xbox, NYT, 2.6.2009,
http://www.nytimes.com/2009/06/02/technology/companies/02soft.html?hpw
Obama’s Face (That’s Him?) Rules the Web
May 31, 2009
Thje New York Times
By RANDY KENNEDY
Mimi Torchia Boothby’s job as a technician puts her outside a wind tunnel
every weekday at the Boeing plant south of Seattle, but in her free time two
years ago she took up watercolors. Among her favorite subjects are cats, idyllic
scenes of Italy — and, of course, Barack Obama, whose contemplative,
sun-splashed portrait she completed a few weeks after his election as president.
She was so happy with it she started offering fine prints of it on the Web, her
first proud professional act as an artist, and has since sold more than two
dozen at $40 apiece. “Talk about viral,” Ms. Boothby, 57, said. “Most of the
people who bought them were people I didn’t even know.”
Perhaps not since John F. Kennedy, whose dusty portraits can still be seen in
kitchens and barbershops and alongside the antique beer cans at bars like
Manuel’s Tavern in Atlanta, has a presidency so fanned the flames of painterly
ardor among hobbyist and professional artists.
Mr. Obama’s campaign was well known for inspiring art, including Shepard
Fairey’s ubiquitous “Hope” poster, a version of which is now in the National
Portrait Gallery in Washington. Months after the election, with the glow of the
administration’s first 100 days dimming, it might have been expected that
enthusiasm for Obama art would be dimming, too.
Yet the still-ample offerings of original paintings of the president and the
first family on eBay and at places like the annual Affordable Art Fair in New
York — along with a crop of presidential-art-obsessed Internet sites including
obamaartreport.com, artofobama.com and, inevitably,
badpaintingsofbarackobama.com — are indications that it might just be a growth
industry.
The phenomenon has been a boon to the near-anonymous painting factories crowded
together in the suburbs of Shenzhen, China, famous for cranking out copies of
masterpieces, along with landscapes and semitasteful nudes. Another one,
seemingly based in Germany, offers stately Obamas amid air-brushy likenesses of
Tupac Shakur, Bruce Lee and Al Pacino (in his “Scarface” role), advertised as
“real hand-embellished” paintings on canvas.
Market interest has also helped small-time artists like Dan Lacey, of tiny Elko,
Minn., a self-described disillusioned conservative who made a name for himself
last year in the blogosphere with his inexplicably strange portraits of Senator
John McCain and Gov. Sarah Palin depicted with pancakes stacked on top of their
heads.
Lately, he has turned to Mr. Obama, cranking out both eBay-ready conventional
portraits — “I hate to say this, but I can do ones like that in about an hour,”
he said — and even stranger works that have tended toward portrayals of the 44th
president naked on a unicorn, often performing gallant deeds like wrestling a
bear on Wall Street or taking the controls of the US Airways flight that landed
in the Hudson River.
“There’s a consistent demand for Obama, both for things that are funny and also
for the serious, sort of Aaron Shikler kinds of treatments,” said Mr. Lacey,
referring to the artist who painted well-known portraits of the Kennedy family.
Among Mr. Lacey’s eBay customers are Carla Pasley, an administrator for a
consumer products company in Kansas City, Mo., who said she is generally
apolitical but bought an Obama portrait simply because she found it “really
pretty,” and Gary Rogers Wares, a manager at a stationery and gift manufacturer
in Culver City, Calif., who has a gold-hued Obama in his office behind his desk
and just won another one at auction for $28.
“I wanted a painting because it’s something unique, and as far as I’m concerned
it’s unique, just like our president is,” Mr. Wares said. “This is historic and
you want something that feels like an heirloom.”
The White House, asked if the president and first lady commonly received gifts
of paintings of themselves, responded with characteristic reticence: “On
background, I can pass along that among other things, the Obamas are given works
of art that include images of the President and symbols from the campaign,” a
spokesman wrote.
If Mr. Obama has not yet fixed the country’s economy or solved its security
problems, he at least seems to have postponed the withering of original art’s
“aura,” or power, in a world of easy reproduction, as famously foreseen by the
philosopher Walter Benjamin.
Indeed, a 90-day search by eBay under the category of Obama paintings, most of
them original creations, not posters or prints, found 787 works offered for sale
from mid-February to mid-May, generating almost $20,000 at an average price of
$118 a painting, said Karen Bard, a spokeswoman. Production generally seems to
be running well ahead of demand.
High-dollar works by well-known artists seem not to fare as well — an Obama
painting by Peter Max listed with a buy-it-now price of $17,000 has had no
takers so far. But paintings in a wild variety of styles — Cubist, Pop,
post-Impressionist, folk arty, street arty and what might be described as
neo-Tolkienesque — have sold in the two-figure and even three-figure range.
Gabriel McGovern, a Web designer in Portland, Ore., who started artofobama.com
during the presidential campaign last summer, said he had not intended to
continue it past the election but had been receiving such a steady stream of
submissions — commercial works, personal works, works photographed on the
streets, 300 or so images of paintings and other kinds of art that he has not
yet had time to post — that he decided to keep the site going.
“My favorites are the first-time painters,” he said. “It might not even really
look like Obama — in fact, not much at all — but they not only paint it, they go
out and find a forum on the Web where they can post it so everyone can see it.”
Ms. Boothby said she is now managing to make a little money on the side with her
brushes and easel and credits Mr. Obama. “I think that portrait I did of the
president was kind of a touchstone for my confidence, painting-wise,” she wrote
in an e-mail message. “I’m not sure I would have been able to start doing
commissions if I hadn’t gotten as warm a reception as I did for that one
painting.”
Mr. Lacey, who admits to parting with paintings for as little as $1 on the Web,
said he sold his president-wrestling-a-bear fantasia for $600 and recently
received a commission for a unicorn-themed Obama. He intends to ride the surging
presidential art wave as long as it will keep him afloat.
During the previous administration, he said, he had also tried his hand at some
portraits of George W. Bush but added, in a tone that mingled regret with
professional candor, “You really couldn’t sell them.”
Obama’s Face (That’s
Him?) Rules the Web, NYT, 31.5.2009,
http://www.nytimes.com/2009/05/31/arts/design/31pain.html?hp
Pentagon Plans New Arm to Wage Wars in Cyberspace
May 29, 2009
The New York Times
By DAVID E. SANGER and THOM SHANKER
WASHINGTON — The Pentagon plans to create a new military command for
cyberspace, administration officials said Thursday, stepping up preparations by
the armed forces to conduct both offensive and defensive computer warfare.
The military command would complement a civilian effort to be announced by
President Obama on Friday that would overhaul the way the United States
safeguards its computer networks.
Mr. Obama, officials said, will announce the creation of a White House office —
reporting to both the National Security Council and the National Economic
Council — that will coordinate a multibillion-dollar effort to restrict access
to government computers and protect systems that run the stock exchanges, clear
global banking transactions and manage the air traffic control system.
White House officials say Mr. Obama has not yet been formally presented with the
Pentagon plan. They said he would not discuss it Friday when he announced the
creation of a White House office responsible for coordinating private-sector and
government defenses against the thousands of cyberattacks mounted against the
United States — largely by hackers but sometimes by foreign governments — every
day.
But he is expected to sign a classified order in coming weeks that will create
the military cybercommand, officials said. It is a recognition that the United
States already has a growing number of computer weapons in its arsenal and must
prepare strategies for their use — as a deterrent or alongside conventional
weapons — in a wide variety of possible future conflicts.
The White House office will be run by a “cyberczar,” but because the position
will not have direct access to the president, some experts said it was not
high-level enough to end a series of bureaucratic wars that have broken out as
billions of dollars have suddenly been allocated to protect against the computer
threats.
The main dispute has been over whether the Pentagon or the National Security
Agency should take the lead in preparing for and fighting cyberbattles. Under
one proposal still being debated, parts of the N.S.A. would be integrated into
the military command so they could operate jointly.
Officials said that in addition to the unclassified strategy paper to be
released by Mr. Obama on Friday, a classified set of presidential directives is
expected to lay out the military’s new responsibilities and how it coordinates
its mission with that of the N.S.A., where most of the expertise on digital
warfare resides today.
The decision to create a cybercommand is a major step beyond the actions taken
by the Bush administration, which authorized several computer-based attacks but
never resolved the question of how the government would prepare for a new era of
warfare fought over digital networks.
It is still unclear whether the military’s new command or the N.S.A. — or both —
will actually conduct this new kind of offensive cyberoperations.
The White House has never said whether Mr. Obama embraces the idea that the
United States should use cyberweapons, and the public announcement on Friday is
expected to focus solely on defensive steps and the government’s acknowledgment
that it needs to be better organized to face the threat from foes attacking
military, government and commercial online systems.
Defense Secretary Robert M. Gates has pushed for the Pentagon to become better
organized to address the security threat.
Initially at least, the new command would focus on organizing the various
components and capabilities now scattered across the four armed services.
Officials declined to describe potential offensive operations, but said they now
viewed cyberspace as comparable to more traditional battlefields.
“We are not comfortable discussing the question of offensive cyberoperations,
but we consider cyberspace a war-fighting domain,“ said Bryan Whitman, a
Pentagon spokesman. “We need to be able to operate within that domain just like
on any battlefield, which includes protecting our freedom of movement and
preserving our capability to perform in that environment.”
Although Pentagon civilian officials and military officers said the new command
was expected to initially be a subordinate headquarters under the military’s
Strategic Command, which controls nuclear operations as well as cyberdefenses,
it could eventually become an independent command.
“No decision has been made,” said Lt. Col. Eric Butterbaugh, a Pentagon
spokesman. “Just as the White House has completed its 60-day review of
cyberspace policy, likewise, we are looking at how the department can best
organize itself to fill our role in implementing the administration’s
cyberpolicy.”
The creation of the cyberczar’s office inside the White House appears to be part
of a significant expansion of the role of the national security apparatus there.
A separate group overseeing domestic security, created by President George W.
Bush after the Sept. 11 attacks, now resides within the National Security
Council. A senior White House official responsible for countering the
proliferation of nuclear and unconventional weapons has been given broader
authority. Now, cybersecurity will also rank as one of the key threats that Mr.
Obama is seeking to coordinate from the White House.
The strategy review Mr. Obama will discuss on Friday was completed weeks ago,
but delayed because of continuing arguments over the authority of the White
House office, and the budgets for the entire effort.
It was kept separate from the military debate over whether the Pentagon or the
N.S.A. is best equipped to engage in offensive operations. Part of that debate
hinges on the question of how much control should be given to American spy
agencies, since they are prohibited from acting on American soil.
“It’s the domestic spying problem writ large,” one senior intelligence official
said recently. “These attacks start in other countries, but they know no
borders. So how do you fight them if you can’t act both inside and outside the
United States?”
John Markoff contributed reporting from San Francisco.
Pentagon Plans New Arm to Wage Wars in
Cyberspace, NYT, 29.5.2009,
http://www.nytimes.com/2009/05/29/us/politics/29cyber.html
Bloodied by Google, Microsoft Tries Again on Search
May 29, 2009
The New York Times
By MIGUEL HELFT
REDMOND, Wash. — Microsoft has been bloodied and repeatedly humbled in its
battle with Google in online search.
That explains why Steven A. Ballmer, the typically bullish and boisterous chief
executive of Microsoft, is speaking cautiously about his company’s latest volley
against Google — a new version of its search engine that Mr. Ballmer was
scheduled to demonstrate publicly for the first time at a technology conference
on Thursday.
“I’m optimistic that we’re taking a big first step,” Mr. Ballmer said in an
interview last week at Microsoft’s headquarters here. “And yet I want to be
realistic. We’ve got to take a lot more steps.”
There have already been many missteps. Despite investing billions of dollars in
its search engine technology over the years, Microsoft has watched Google
steadily eat away at its market share. This time it is taking a more targeted
approach, working to help searchers with specific online tasks. It will back its
latest release with one of the biggest marketing efforts in its history. And it
has come up with a new name, Bing, that will replace the confusing Live Search.
The stakes for Microsoft couldn’t be higher. Search has become the central tool
for navigating the Web, and ads tied to search results are becoming an ever more
important piece of the advertising market.
Microsoft is so eager to catch up that it bid nearly $50 billion last year to
buy Yahoo, the No. 2 search company behind Google. Mr. Ballmer is no longer
interested in buying Yahoo but still hopes the two companies will find a way to
team up to take on Google in search, and talks on a partnership are continuing.
For now, however, Microsoft is proceeding on its own. Bing represents the fruit
of more than a year of research showing that while users say they are generally
satisfied with Web search services, their behavior suggests that they often
stumble as they rely on search engines to complete tasks like deciding what
camera to buy, where to go on a trip or how to better understand their latest
medical diagnosis. Bing offers an array of new features that are aimed at
simplifying those tasks, and it will eventually expand to cover more of them.
“We are pushing beyond the way search works today,” said Yusuf Mehdi, senior
vice president of Microsoft’s online audience business group.
The most noticeable new feature in Bing is what Microsoft executives call a
table of contents, a navigation rail that allows users to refine their searches
and that changes with each query. A search for Taylor Swift, for instance, gives
users the option to quickly zero in on things like images, videos, lyrics and
tickets. A search for Elvis Presley will offer slightly different options — no
tickets, but a fan club.
In a search for Honda Civic, the top refinement is “used,” but in one for
Hyundai Sonata it is “problems,” because search data suggest that those are the
most frequent follow-up queries associated with those cars.
In many cases, Bing also extracts information from Web pages and presents it an
easy-to-digest format. A search for U.P.S. will deliver a search box to track
parcels, as well as a phone number for customer service. A search for
“Terminator Salvation” will display movie showtimes at nearby theaters.
Bing also presents more detailed results in four search categories — travel,
health, shopping and local. In browsing the shopping area for a Canon camera,
for instance, Bing extracts and displays information from reviews covering
things like image quality and size.
Bing, which will be available to the public by next Wednesday at www.bing.com,
is not alone in its evolution away from the traditional 10 blue links that
search engines have displayed for years. Google, for instance, has long blended
images, news articles and videos in search results, and recently began offering
ways to refine searches. Yahoo also presents movie times and is working to
extract information like reviews from Web pages. But with Bing, Microsoft
appears to have pushed the changes deeper and into more subject areas than its
rivals.
Whether that translates into success depends on many unknowns, including whether
Microsoft’s search results are generally as helpful as Google’s, as the
company’s executives promise.
“There are things where they are going to be superior to Google,” said Danny
Sullivan, a search expert and the editor of the SearchEngineLand blog. “But it
is not a game changer. The features are not going to instantly compel people to
switch.”
Mr. Sullivan said Microsoft’s best hope is that users begin spreading the word
to friends about the features of Bing that they like. “That can really resonate
with people,” he said. But Mr. Sullivan also cautioned that Google may be able
to quickly match anything that Microsoft has done that proves compelling with
users.
Others say Microsoft’s biggest challenge may be convincing enough users to give
Bing a try.
“There is not a perceived market problem with search that needs fixing,” said
Bryan Wiener, chief executive of 360i, a digital marketing agency. “They have a
marketing challenge in convincing consumers that there is reason to look beyond
Google.”
That is where Bing’s marketing campaign comes in. The company is planning to
spend well in excess of $100 million, making this one of its biggest campaigns
ever. When deals with partners are included, like agreements that have already
been announced with Hewlett-Packard, Dell and Verizon to give the search engine
prime placement on PCs and phones, the marketing effort reaches to several
hundred million dollars, according to people familiar with Bing’s marketing plan
who asked not to be named because its details are confidential.
In April, Microsoft accounted for 8.2 percent of searches in the United States,
a fraction of Google’s 64.2 percent, according to comScore. Yahoo’s share was
20.4 percent. Mr. Ballmer is confident that with Bing, Microsoft can begin
clawing its way back up the share rankings soon.
“I hope over the next year we’ll see small results,” Mr. Ballmer said. His
confidence mixed with a heavy dose of realism, he added: “Big as a percentage of
our share and small as a percentage, maybe, of Google’s share.”
Bloodied by Google, Microsoft Tries Again on
Search, NYT, 29.5.2009,
http://www.nytimes.com/2009/05/29/technology/companies/29soft.html?hp
Microsoft Adds Touch Screen, Web Browser to Zune
May 27, 2009
Filed at 9:11 a.m. ET
By THE ASSOCIATED PRESS
The New York Times
REDMOND, Wash. (AP) -- Microsoft Corp. says the next generation of its Zune
music player due out in the fall will have a touch screen, Wi-Fi Internet access
and high-definition radio receiver.
The new device, called the Zune HD, will carry a full Web browser and a
high-definition video output that will allow users to play files through a
docking station on HD televisions, Microsoft said late Tuesday.
The Zune will also sport an organic light-emitting diode screen, a technology
that helps improve battery life and image quality.
The new features ramp up Microsoft's effort to compete with Apple Inc. products
such as the iPod Touch, and highlight the company's push to integrate different
platforms, from PCs and mobile phones to the Xbox.
Microsoft also announced Tuesday that this fall its Zune music service will
serve Xbox Live subscribers for the first time.
The company said it will demonstrate how the new Zune and Xbox link up ''to
create a game-changing entertainment experience'' at the Electronic
Entertainment Expo next week.
Microsoft Adds Touch
Screen, Web Browser to Zune, NYT, 28.5.2009,
http://www.nytimes.com/aponline/2009/05/27/business/AP-US-Microsoft-Zune.html
Aided by Poker Devotees, Lawmaker Pushes to End the Ban on
Online Gambling
May 26, 2009
The New York Times
By BERNIE BECKER
WASHINGTON — After coming up short in a first effort, a Democratic lawmaker
has again introduced legislation that would roll back a ban on Internet gambling
enacted when Republicans led Congress.
The legislation, introduced this month by Representative Barney Frank of
Massachusetts, would allow the Treasury Department to license and regulate
online gambling companies that serve American customers. Under the current law,
approved by Congress in September 2006, financial institutions are banned from
handling transactions made to and from Internet gambling sites.
At a news conference announcing the legislation, Mr. Frank, who is chairman of
the House Financial Services Committee, pointed out that the federal government
could collect increased tax revenues if Internet gambling was regulated. But he
said online gambling should be legal as a matter of personal liberty, calling it
an activity the government should neither encourage nor prohibit.
“Most actions the government should stay out of,” Mr. Frank said.
Mr. Frank’s bill has roughly two dozen co-sponsors, most of them Democrats. He
did not seek the backing of the Obama administration or the leadership in either
the House or the Senate.
The legislation does have the backing of those who enjoy poker. The Poker
Players Alliance, one of the groups lobbying for the bill’s passage, says it has
more than a million members and, in former Senator Alfonse M. D’Amato,
Republican of New York, a well-known chairman to press its case on Capitol Hill.
Opponents are mobilizing to defeat the bill. They include social conservatives
and professional and amateur sports organizations, which say more gambling
opportunities could threaten the integrity of their competition.
“Illegal offshore Internet gambling sites are a criminal enterprise, and
allowing them to operate unfettered in the United States would present a clear
danger to our youth, who are subject to becoming addicted to gambling at an
early age,” Representative Spencer Bachus, Republican of Alabama and the ranking
member on the House Financial Services Committee, said in a statement.
The legislation differs somewhat from a bill Mr. Frank introduced in 2007, which
never made it out of committee. For example, this bill forbids betting on sports
events, while the earlier one let sports organizations decide themselves whether
to prohibit online betting on their games.
Like the previous version, the bill allows states and Indian tribal lands to opt
out if they do not want their residents using licensed Web sites. It also
requires companies seeking a license to employ safeguards that supporters say
would do a great deal to prevent minors from gaining access to gambling sites
and help combat compulsive gambling.
“The technology is out there,” said John Pappas, executive director of the Poker
Players Alliance. “It’s been tested regularly. And those who fail to use it will
lose their license.”
Not everyone has been convinced.
The American Gaming Association, which lobbies for the casino industry, says it
will remain neutral on Mr. Frank’s bill, as it did when the ban was enacted.
Frank J. Fahrenkopf Jr., the association’s president, said opinions within the
group on Internet gambling ran the gamut. Some members are for online gambling
in any form, while others prefer a system run by individual states. Opponents
worry that Internet gambling will take customers away from their casinos and
that it cannot be properly regulated.
Despite the language banning sports betting, the four major professional sports
leagues and the National Collegiate Athletic Association believe the bill could
in fact encourage gambling on games. In a strongly worded letter to the House
Financial Services Committee, the groups said the legislation “reverses nearly
50 years of clear federal policy against sports betting and it opens the door
wide to sports gambling on the Internet.”
Mr. Bachus remains skeptical about age verification technology and other
safeguards, citing 2007 testimony from an Internet security expert before his
committee asserting that such “security measures are inherently unreliable, can
be trivially circumvented and will fail at high rates.”
Mr. Frank said he believed lobbying by poker players and other fans of online
gambling could help reverse the ban. He said he intended to move the bill
through his committee before Congress began its break in August.
“Congress kind of sneaked up on the American people,” Mr. Frank said of the
online gambling ban. “The people woke up.”
But there could be at least one powerful roadblock. The Senate majority leader,
Harry Reid, Democrat of Nevada, has opposed lifting the ban in the past,
questioning whether the government could effectively regulate Internet gambling.
And a statement released from his office recently suggested that he had other
concerns, as well.
“Gaming is an important industry to the state, and anything that affects it will
be reviewed carefully,” said Jim Manley, Mr. Reid’s spokesman.
Aided by Poker Devotees,
Lawmaker Pushes to End the Ban on Online Gambling, NYT, 26.5.2009,
http://www.nytimes.com/2009/05/26/us/politics/26cong.html?hpw
'Keyboard Cat' Phenomenon Spreads on Web, TV
May 22, 2009
Filed at 7:30 a.m. ET
By THE ASSOCIATED PRESS
The New York Times
NEW YORK (AP) -- A new Internet phenomenon has drawn the interest of millions
-- including Stephen Colbert.
One of the most popular current online crazes is something called ''Play Him
Off, Keyboard Cat,'' a user-generated video meme.
The formula is a simple. A clip is played of a pratfall or some unfortunate,
self-inflicted accident. This is immediately followed by (always the same) old
clip of a cat playing an upbeat tune on a keyboard.
The keyboard cat is, in a way, the smiling face of fate, perpetually making
light of silly human failures. It's not stupid pet tricks, it's stupid people
tricks. Like the old vaudeville hook, the keyboard cat will play you off the
stage.
The phenomenon was started by Brad O'Farrell, a 22-year-old syndication manager
for the video Web site MyDamnChannel.com. In February, he uploaded the first
video: a clip of someone falling down an escalator, promptly ''played off'' by
the taunting keyboard cat.
The video has spawned hundreds of copycats that have collectively been watched
by millions. One shows a commentator on Fox News passing out on screen; another
features a failed marriage proposal.
''I did kind of try to make it a video that other people could repeat easily,''
said O'Farrell. ''The original clip of the cat playing the keyboard, I was
already sending to people ... following bad news.''
The trend even jumped to ''The Daily Show'' recently. While Jon Stewart did the
''toss'' to ''The Colbert Report,'' Colbert worried he would make a mistake and
be mocked by the keyboard cat. Sure enough, Colbert stumbled over a line and the
keyboard cat gave him the hook.
''Every time it gets to a larger media outlet, I assume that's the biggest one
that's going to happen,'' said O'Farrell.
O'Farrell made the video with the permission of Charlie Schmidt, who created the
original keyboard cat video two decades ago. O'Farrell links his video to
Schmidt's site to help Schmidt benefit from all the traffic.
Schmidt, a performance artist, made the video by manipulating the shoulders of
his cat, Fatso, so his paws touched the keyboard. Fatso may be long dead, but
he's having the last laugh.
------
On the Net:
http://www.youtube.com/user/BradOFarrell
http://www.charlieschmidt.com
'Keyboard Cat'
Phenomenon Spreads on Web, TV, NYT, 22.5.2009,
http://www.nytimes.com/aponline/2009/05/22/arts/AP-US-Web-Keyboard-Cat-Sensation.html
Many Twitters Are Quick Quitters, Finds Study
April 29, 2009
Filed at 10:20 a.m. ET
By REUTERS
The New York Times
SYDNEY (Reuters) - Today's Twitters are often tomorrow's quitters, according
to data that questions the long-term success of the latest social networking
sensation used by celebrities from Oprah Winfrey to Britney Spears.
Data from Nielsen Online, which measures Internet traffic, found that more than
60 percent of Twitter users stopped using the free social networking site a
month after joining.
"Twitter's audience retention rate, or the percentage of a given month's users
who come back the following month, is currently about 40 percent," David Martin,
Nielsen Online's vice president of primary research, said in a statement.
"For most of the past 12 months, pre-Oprah, Twitter has languished below 30
percent retention."
San Francisco-based Twitter was created three years ago as an Internet-based
service that could allow people to follow the 140-character messages or "tweets"
of friends and celebrities which could be sent to computer screens or mobile
devices.
But it has enjoyed a recent explosion in popularity on the back of celebrities
such as actor Ashton Kutcher and U.S. talk show host Oprah Winfrey singing its
praises and sending out "tweets" which can alert readers to breaking news or the
sender's sometimes mundane activities.
President Barack Obama used Twitter during last year's campaign and other
prominent celebrities on Twitter include basketballer Shaquille O'Neal and
singers Britney Spears and Miley Cyrus.
Twitter, as a private company, does not disclose the number of its users but
according to Nielsen Online, Twitter's website had more than 7 million unique
visitors in February this year compared to 475,000 in February a year ago.
But Martin said a retention rate of 40 percent will limit a site's growth to a
10 percent reach figure over the longer term.
"There simply aren't enough new users to make up for defecting ones after a
certain point," he said in a statement.
Martin said Facebook and MySpace, the more established social network sites,
enjoyed retention rates that were twice as high and those rates only rose when
they went through their explosive growth phases.
Both currently have retention rates of about 70 percent with Facebook having
about 200 million users.
"Twitter has enjoyed a nice ride over the last few months, but it will not be
able to sustain its meteoric rise without establishing a higher level of user
loyalty," said Martin.
(Writing by Belinda Goldsmith, Editing by Miral Fahmy)
Many Twitters Are Quick
Quitters, Finds Study, NYT, 29.4.2009,
http://www.nytimes.com/reuters/2009/04/29/technology/tech-us-twitter.html
Justice Dept. Opens Antitrust Inquiry Into Google Books Deal
April 29, 2009
The New York Times
By MIGUEL HELFT
SAN FRANCISCO — The Justice Department has begun an inquiry into the
antitrust implications of Google’s settlement with authors and publishers over
its Google Book Search service, two people briefed on the matter said Tuesday.
Lawyers for the Justice Department have been in conversations in recent weeks
with various groups opposed to the settlement, including the Internet Archive
and Consumer Watchdog. More recently, Justice Department lawyers notified the
parties to the settlement, including Google, and representatives for the
Association of American Publishers and the Authors Guild, that they were looking
into various antitrust issues related to the far-reaching agreement.
The inquiry does not necessarily mean that the department will oppose the
settlement, which is subject to a court review. But it suggests that some of the
concerns raised by critics, who say the settlement would unfairly give Google an
exclusive license to profit from millions of books, have resonated with the
Justice Department.
A spokeswoman for the Justice Department was not immediately available to
comment. A spokesman for Google declined to comment. Representatives for the
Association of American Publishers and the Authors Guild could not immediately
be reached.
The settlement agreement stems from a class action filed in 2005 by the Authors
Guild and the Association of American Publishers against Google. The suit
claimed that Google’s practice of scanning copyrighted books from libraries for
use in its Book Search service was a violation of copyrights.
The settlement, announced in October, gives Google the right to display the
books online and to profit from them by selling access to individual texts and
selling subscriptions to its entire collection to libraries and other
institutions. Revenue would be shared among Google, authors and publishers.
But critics say that Google alone would have a license that covers millions of
so-called orphan books, whose authors cannot be found or whose rights holders
are unknown. Some librarians fear that with no competition, Google will be free
to raise prices for access to the collection.
Separately on Tuesday, Judge Denny Chin of Federal District Court in New York,
who is overseeing the settlement, postponed by four months the May 5 deadline
for authors to opt out of the settlement and for other parties to oppose it or
file briefs. The decision follows requests by groups of authors and their heirs,
who argued that authors needed more time to review the settlement.
Google, as well as the authors and publishers, have defended the settlement,
saying it will bring benefits to authors, publishers and the public. They say it
will renew access to millions of out-of-print books.
If the Justice Department decides to take action against the settlement, it will
not be the first time that Google has found itself in the sights of federal
regulators. Last year, Google abandoned a prominent advertising partnership with
Yahoo after the department threatened to go to court to block the deal.
The Justice Department and the Federal Trade Commission have wrangled over
jurisdiction over the book settlement, and the Justice Department won out,
according to a person familiar with the inquiry.
Justice Dept. Opens
Antitrust Inquiry Into Google Books Deal, NYT, 29.4.2009,
http://www.nytimes.com/2009/04/29/technology/internet/29google.html
Facebook Users' Vote Ending Way Short of Threshold
April 23, 2009
The New York Times
By THE ASSOCIATED PRESS
Filed at 11:33 a.m. ET
NEW YORK (AP) -- Facebook invited the 200 million people who regularly use
the site to vote on its governing documents. But it's unclear how much of a
difference it will make.
Facebook launched the vote after concerns erupted about who controls users'
personal information. The site gave its members until Thursday afternoon to
choose either the current terms of use, or a revised set of documents that
reflect input from users over the past 30 days.
However, Facebook said the vote would be binding only if 30 percent of the
site's active users voted. That would be 60 million people.
On Thursday morning, a vote on the site revealed that about 609,000 people had
cast ballots. Spokesman Barry Schnitt says Facebook plans to announce the
results and ''next steps'' Friday.
Facebook Users' Vote
Ending Way Short of Threshold, NYT, 23.4.2009,
http://www.nytimes.com/aponline/2009/04/23/business/AP-US-TEC-Facebook-Vote.html
Google to Target Ads Based on Online Activity
March 12, 2009
Filed at 3:15 a.m. ET
The New York Times
By REUTERS
SAN FRANCISCO (Reuters) - Google Inc will begin to aim online ads at people
based on their Web browsing history, joining an industry trend that has raised
privacy concerns even as it makes product pitches more effective.
The new program, dubbed "interest based" advertising, is being rolled out on a
test basis across Google's network of partner websites and on its video-sharing
site YouTube, according to an announcement on Google's blog on Wednesday.
The move comes a few weeks after the Web search leader's smaller rival, Yahoo
Inc, unveiled its own advertising enhancements, which rely on an individual's
online activity.
While behavioral ad techniques have been around for several years, some past
efforts have raised privacy concerns, and Google has refrained from offering
such advertising until now.
"Advertisers are under increasing pressure to be able to tie as much marketing
spend as they can to direct sales revenue," said Andrew Frank, an analyst at
market research firm Gartner.
Shares of Google rose $9.74, or 3.16 percent, to $317.91 on Nasdaq.
Until now, the types of text and display ads that Google served to Web surfers
were based solely on the content of the specific Web page being viewed by an
individual.
With behavior advertising, Google and advertisers will be able to consider an
individual's broader history of Web surfing when deciding which ads to pitch.
"If, for example, you love adventure travel and therefore visit adventure travel
sites, Google could show you more ads for activities like hiking trips to
Patagonia or African safaris," Google Vice President of Product Management Susan
Wojcicki explained on Google's blog, adding that advertisers have been asking
Google for such features for a long time.
Advertising based on consumer interest or behavior have the potential to
increase consumer response and so-called click-through rates, which translates
into higher ad revenue for the sites.
But U.S. lawmakers held hearings last year on behavioral advertising, after
concerns arose when a company called NebuAd, in a deal with cable company
Charter Communication, disclosed a pilot program to track customers.
Congressman Rick Boucher, head of the telecom subcommittee of the House of
Representative's Energy and Commerce, has said the issue will be a top priority
this year. The Virginia Democrat's office had no immediate comment on Google's
plans.
MORE REGULATION?
The U.S. Federal Trade Commission recently expanded its voluntary guidance on
how websites inform consumers that their data is being collected, to include
mobile and Internet companies. Regulators have warned that failure to comply
would lead to tougher regulation.
In announcing the initiative on Wednesday, Google said privacy issues were an
important consideration. "This kind of tailored advertising does raise questions
about user choice and privacy -- questions the whole online ad industry has a
responsibility to answer," Wojcicki said in the blog post.
Google said it has three key safeguards: consumers can choose to opt out of the
program; consumers can edit their profile of preferences based on online
activity; and consumers can click on a button to learn how an ad was pitched to
them.
Marc Rotenberg, executive director of the Electronic Privacy Information Center,
said that regardless of Google's efforts to address privacy concerns, the
company's new ad program "throws up red flags" for Internet privacy.
"This is the Internet's largest search company now profiling and tracking
Internet users. That shouldn't happen," said Rotenberg. He said his organization
was evaluating "possibilities" about a potential response to Google's move, but
declined to specify what options were under consideration.
But Ari Schwartz, vice president of the Center for Democracy and Technology,
said there are positives in Google's plan, including users getting access to
their own profile.
"On balance it is a step in the right direction," said Schwartz, whose group was
consulted while Google developed its plan. But he noted that Google plans to
still rely on consumers opting out, rather than in, which most of the public
opposes.
Google, the No.1 Internet search engine in the United States, generates 97
percent of its revenue from advertising. Much of that comes from text ads that
appear alongside search results.
Google acquired DoubleClick for $3.2 billion in 2008 in order to beef up its
position in the market for display ads.
Adopting behavioral ad techniques is "a logical way for Google to get better at
the display game," said Emily Riley, a senior analyst at Forrester Research.
In particular, she said, the vast size of Google's AdSense network of partner
Web sites and the company's technology could generate valuable data for
marketers and advertisers.
"In theory they should have great scale with the behaviors they're tracking,"
said Riley.
(Reporting by Alexei Oreskovic; Additional reporting by Kim Dixon in
Washington; Editing by Richard Chang)
Google to Target Ads
Based on Online Activity, NYT, 12.3.2009,
http://www.nytimes.com/reuters/2009/03/12/technology/tech-us-google.html
Apple Rolls Out Talking iPod Shuffle
March 11, 2009
Filed at 1:16 p.m. ET
The New York Times
By REUTERS
NEW YORK (Reuters) - Apple Inc introduced a smaller version of its popular
iPod Shuffle music player on Wednesday with a new feature that tells the user
what song is playing.
The new 4-gigabyte gadget costs $79, is half the size of the previous Shuffle,
and carries up to 1,000 songs -- twice as many as the last generation of the
device.
All of the controls on the new Shuffle have been moved from the device to the
earphone cord. The new VoiceOver feature announces songs and playlists to users
in 14 different languages, according to Apple, whose shares rose 4.5 percent.
The voice function is particularly useful on the Shuffle, which does not have a
display screen like most iPods or other digital music players.
Needham & Co analyst Charles Wolf said the new Shuffle design was appealing and
called the voice function a "nice a little gimmick. It shows that Apple intends
to keep that piece of the portfolio going. They're going to continue to
innovate, upgrade the sub-$100 device."
"It won't necessarily stimulate sales, but it clearly will keep sales of the
Shuffle going forward," he said.
The VoiceOver feature works by synchronizing with iTunes software, which
installs a voice kit on the user's computer. VoiceOver can also tell a user how
much battery life remains.
"You previously couldn't have multiple playlists on the iPod Shuffle because you
couldn't really switch between them as there was no way to know how you would
switch," said Greg Joswiak, Apple vice president of iPod marketing, told
Reuters. "So now instead of seeing, you get to hear."
Although Apple does not break out Shuffle sales, Needham's Wolf estimated some
7.5 million units were sold in the December quarter, it's biggest-selling
quarter. Apple sold 22.7 million iPod units overall in the period.
The third generation of iPod Shuffle will be the world's tiniest music player,
smaller than an AA battery. It comes in two colors, silver and black.
Apple will continue to sell the second-generation version of the 1-gigabyte,
240-song Shuffle for $49. but phase out the 2-gigabyte Shuffle, which sells for
$69.
The iPod music player has played an important role in the revival of Apple's
fortunes. The company has sold more than 200 million iPods since they launched
in 2001. It launched the first Shuffle in January 2005.
The refreshed Shuffle comes just a week after the company updated its line of
Mac desktop computers. Apple refreshed it MacBook laptop computers last fall.
Shares of Cupertino, California-based Apple rose $3.97 to $92.59 in early
afternoon trading on Nasdaq.
(Reporting by Yinka Adegoke and Gabriel Madway; Editing by Derek Caney, Steve
Orlofsky and Jeffrey Benkoe)
Apple Rolls Out Talking
iPod Shuffle, NYT, 11.3.2009,
http://www.nytimes.com/reuters/2009/03/11/technology/tech-us-apple.html
The TV Watch
Fallon Faces the Camera, Conscious of the Web
March 6, 2009
The New York Times
By ALESSANDRA STANLEY
He looked nervous, even flustered, at first, and some of the prepared comedy
was surprisingly lame. That doesn’t matter. Jimmy Fallon’s first few days don’t
really reveal how “Late Night With Jimmy Fallon” will fare.
Monitoring the opening kinks and experiments of a new talk show is a spectator
sport, and this entry comes with an added “American Idol” edge: NBC had the last
word during the auditions, but Internet users are now expected to comment and
cavil interactively and build — or diminish — Mr. Fallon’s television audience.
Mr. Fallon was cute and funny on “Saturday Night Live,” but he is not
necessarily the ideal choice for the “Late Night” core audience of young males:
his humor is mischievous, not anarchic. (If fans had a call-in vote, they might
have elected Jon Stewart or Stephen Colbert.)
Still, Mr. Fallon is engaging and has an antic, quick-witted charm. He seemed
more confident by the show’s third night and, oddly enough, had better comic
chemistry with Cameron Diaz on Wednesday than with Tina Fey, his former “Weekend
Update” co-anchor on “SNL,” the night before. Most of his skits and routines,
however, seemed written for the Web, not for broadcast.
It’s still too soon to pass judgment on Mr. Fallon’s talents as a talk show
host, but it’s a perfectly good time to examine NBC’s latest test of synergy,
the marriage of the Internet and a television show.
Almost all shows nowadays have Web sites with extraneous videos, fan blogs and
viewer e-mail exchanges. But Mr. Fallon has gone further to co-opt the Internet
than either of his two network rivals, Jimmy Kimmel on ABC and Craig Ferguson on
CBS, or even cable upstarts like Chelsea Handler, the host of “Chelsea Lately”
on E! In the months leading up to his debut on Monday, Mr. Fallon tried to pump
up younger viewers’ interest with “Late Night” Webisodes. He has pages on
Facebook, Myspace and Twitter.
Perhaps accordingly, many of the routines he worked into the show in its first
nights might have been better suited to YouTube. And that youth-oriented
material clashes with the highly conventional, even fusty jokes in his opening
monologue (“Everybody’s cutting back, everybody: Madonna’s now down to one
teenage boyfriend”), as well as with the choice of a veteran actor, Robert De
Niro, to be his first guest.
Twitter is so overexposed that it has become a joke, but Mr. Fallon apparently
isn’t in on it. He interviewed Ms. Diaz by posing questions submitted via
Twitter. Those turned out to be as dull and anodyne as any taken from a live
audience. (“If Cameron wasn’t acting, what would her dream job be?” Ms. Diaz
didn’t have a ready answer, so Mr. Fallon supplied it: “Forest ranger.”)
Wednesday’s quite funny parody of romance novels, “bromance novels,” came with a
link on the show’s Web site (latenightwithjimmyfallon.com) that allows users to
watch a video of the shooting of the cover art.
Mr. Fallon consistently tried to incorporate a wackier Web spirit into his
on-air performance, even picking random people in the studio audience and
assigning them made-up Facebook identities. None were very funny.
Remarkably, given how many months he has had to prepare, many of his supposedly
wacky, Web-style pranks were oddly plodding and unimaginative. On the first
night three audience members were invited onstage to lick something in exchange
for $10. The things were all inanimate objects: a lawn mower, a copier, a
fishbowl. The slow-motion “super-sexy replay” was funny once, not three times.
Mr. Fallon does not have a sidekick, but he does have a cool band, the Roots,
whose musicians are deadpan and steadfastly underwhelmed by his jokes, and over
time that could serve as a comic foil to his eager-to-please persona.
There were other amusing moments, including a random, bizarre video of German
soccer players dancing that was found on the Web and a mock charitable appeal
for laid-off Wall Street workers, a Save the Bankers Foundation, that could have
just as easily been a “Saturday Night Live” skit.
And Mr. Fallon got better, and more relaxed, after his debut, though he joked
with Tina Fey about his “flop sweat” moment with Mr. De Niro. (When performers
admit to being nervous, it’s a little like a woman on a date bemoaning how fat
she is: nobody wants to hear it.)
The first days are tough because large audiences tune in to see what all the
prepremiere fuss was about, boosting ratings and expectations, then quickly turn
away if not instantly amused. And most hosts go through a trial-and-error
period. Mr. Kimmel started out more loutishly and live; now he is more
buttoned-down, and his show is taped, even though it is still called “Jimmy
Kimmel Live.”
Mr. Ferguson began with a very conventional “Tonight Show” format, then slowly
allowed more of his own offbeat storytelling and Monty Pythonesque
eccentricities into his act.
NBC picked Mr. Fallon, and he can sometimes seem like an old person’s notion of
a hip young comic, but that doesn’t mean that he isn’t funny or that he cannot
hold his own on “Late Night.” Only time, not Twitter, will tell.
Fallon Faces the Camera,
Conscious of the Web, NYT, 6.3.2009,
http://www.nytimes.com/2009/03/06/arts/television/06fall.html
Facebook Withdraws Changes in Data Use
February 19, 2009
The New York Times
By BRAD STONE and BRIAN STELTER
Facebook, the popular social networking site where people share photos and
personal updates with friends and acquaintances, lost some face on Wednesday.
After three days of pressure from angry users and the threat of a formal legal
complaint by a coalition of consumer advocacy groups, the company reversed
changes to its contract with users that had appeared to give it perpetual
ownership of their contributions to the service.
Facebook disavowed any such intentions but said early Wednesday that it was
temporarily rescinding the changes and restoring an earlier version of its
membership contract.
In a message to members, the company, based in Palo Alto, Calif., said it would
collaborate with users to create a more easily understandable document.
Facebook’s chief executive, Mark Zuckerberg, also invited users to contribute to
a new Bill of Rights and Responsibilities, which would serve as a governing
document for the site. Facebook has been redefining notions of privacy while
growing so rapidly that it now has 175 million active users, giving it a
population larger than most countries.
In an interview, Chris Kelly, Facebook’s chief privacy officer, characterized
the event as a misunderstanding, stemming from a clumsy attempt by the company
to simplify its contract with users, called the terms of service.
“We were not trying to make a substantive change in our rights or ability to
control our members’ content on the service at all,” Mr. Kelly said. “As that
misunderstanding became the main theme, we became very concerned and wanted to
communicate very clearly to everyone our intentions by rolling back to the old
terms of service.”
Facebook’s retreat ends a hullabaloo in which tens of thousands of Facebook
members joined groups devoted to protesting the changes and bloggers heaped
scorn and criticism on the company. Facebook sought to limit the damage from an
uproar that in many ways was reminiscent of the flap in 2007 over its Beacon
advertising service.
That project shared details of members’ activities on certain outside sites to
all of their Facebook friends. The Electronic Privacy Information Center, along
with 25 other consumer interest groups, had planned to file a complaint with the
Federal Trade Commission on Wednesday. The complaint was going to claim that
Facebook’s new rules were unfair and deceptive trade practices, because the
company had repeatedly promised users that they owned their content but appeared
to be saying something else in its revised terms.
The center, based in Washington, was prepared to argue that Facebook’s new rules
were meant to accompany changes to the site that would give developers and
advertisers the ability to access users’ contributions, like status updates,
which many members use to reveal details about their lives, for example, where
they are traveling.
“This was a digital rights grab,” said Marc Rotenberg, the center’s executive
director. “Facebook was transferring control of user-generated content from the
user to Facebook, and that was really alarming.”
He said Facebook representatives contacted him on Tuesday night to ask whether
his group would refrain from filing the complaint if the company backtracked to
the old language in the contract. Mr. Rotenberg agreed.
Facebook’s retreat can also be credited to the mass of members who made their
voices heard in a strikingly vociferous movement that spanned the globe.
Facebook made the changes to its terms of service on Feb. 6, but they were
highlighted Sunday by a blog called The Consumerist, which reviewed the
contract. The blog, which is owned by Consumers Union, publisher of Consumer
Reports, warned people to “never upload anything you don’t feel comfortable
giving away forever, because it’s Facebook’s now.”
Mr. Kelly of Facebook says that the blog made “substantial misinterpretations,”
including missing a crucial provision that made Facebook’s license to members’
material subject to the user’s individual privacy settings. He conceded,
however, that Facebook did not effectively communicate that nuance.
The Consumerist blog entry set off an explosion of activity that overwhelmed
Facebook’s own attempts to quickly clarify the matter. In a blog post on Monday,
Mr. Zuckerberg tried to reassure users that they still owned and controlled
their own data and that the company had no plans to use it without their
permission.
That did not satisfy Facebook users like Julius Harper, 25. On Monday, he
created a Facebook group to protest the changes. Soon after, he joined with Anne
Kathrine Petteroe, 32, a technology consultant in Oslo, who had started a
similar group.
By Wednesday, more than 100,000 people had joined their efforts and were airing
their concerns, like whether photos they post to the site could appear in ads
without their permission.
“I believe Facebook on this matter, but my issue is that Facebook is not just
one person,” Mr. Harper said. “They could get bought out by anybody, and those
people may not share the good intentions that Mark and his team claim to have.”
Analysts say that much of the confusion and rancor this week stemmed from the
fact that sites like Facebook have created a new sphere of shared information
for which there are no established privacy rules.
E-mail between two people is private, for example, and a post on a message board
is clearly public. But much communication among Facebook members, which is
exposed only to their friends, sometimes on a so-called wall, lies in a middle
ground one might call “semipublic.”
“If I post something on your wall, and then I decide to close my account, what
happens to that wall post?” said Marcia Hofmann, a lawyer with the Electronic
Frontier Foundation, an Internet civil liberties group. “Is that my data or your
data? That’s a very tricky issue, and it’s one that hasn’t come up a whole lot
in the past.”
Facebook Withdraws
Changes in Data Use, NYT, 19.2.2009,
http://www.nytimes.com/2009/02/19/technology/internet/19facebook.html
Melding Obama’s Web to a YouTube Presidency
January 26, 2009
The New York Times
By JIM RUTENBERG and ADAM NAGOURNEY
WASHINGTON — Lyle McIntosh gave everything he could to Barack Obama’s Iowa
campaign. He helped oversee an army that knocked on doors, distributed fliers
and held neighborhood meetings to rally support for Mr. Obama, all the while
juggling the demands of his soybean and corn farm.
Asked last week if he and others like him were ready to go all-out again, this
time to help President Obama push his White House agenda, Mr. McIntosh paused.
“It’s almost like a football season or a basketball season — you go as hard as
you can and then you’ve got to take a breather between the seasons,” he said,
noting he found it hard to go full-bore during the general election.
Mr. McIntosh’s uncertainty suggests just one of the many obstacles the White
House faces as it tries to accomplish what aides say is one of their most
important goals: transforming the YouTubing-Facebooking-texting-Twittering
grass-roots organization that put Mr. Obama in the White House into an
instrument of government. That is something that Mr. Obama, who began his career
as a community organizer, told aides was a top priority, even before he was
elected.
His aides — including his campaign manager — have created a group, Organizing
for America, to redirect the campaign machinery in the service of broad changes
in health care and environmental and fiscal policy. They envision an army of
supporters talking, sending e-mail and texting to friends and neighbors as they
try to mold public opinion.
The organization will be housed in the Democratic National Committee, rather
than at the White House. But the idea behind it — that the traditional ways of
communicating with and motivating voters are giving way to new channels built
around social networking — is also very evident in the White House’s media
strategy.
Like George W. Bush before him, Mr. Obama is trying to bypass the mainstream
news media and take messages straight to the public.
The most prominent example of the new strategy is his weekly address to the
nation — what under previous presidents was a speech recorded for and released
to radio stations on Saturday mornings. Mr. Obama instead records a video, which
on Saturday he posted on the White House Web site and on YouTube; in it, he
explained what he wanted to accomplish with the $825 billion economic stimulus
plan working its way through Congress. By late Sunday afternoon, it had been
viewed more than 600,000 times on YouTube.
The White House also faces legal limitations in terms of what it can do. Perhaps
most notably, it cannot use a 13-million-person e-mail list that Mr. Obama’s
team developed because it was compiled for political purposes. That is an
important reason Mr. Obama has decided to build a new organization within the
Democratic Party, which does not have similar restrictions.
Still, after months of discussion, aides said the whole approach remained a work
in progress, even after Friday, when the organizers e-mailed a link to a video
to those 13 million people announcing the creation of Organizing for America.
Mr. Obama’s aides know they have a huge resource to harness, but fundamental
questions remain about how it will run and precisely what organizers are hoping
to accomplish.
“This has obviously never been undertaken before,” David Plouffe, Mr. Obama’s
campaign manager and one of the organizers of this effort, said in the video
sent to supporters. “So it’s going to be a little trial and error.”
Even with that video, in addition to one sent earlier in the president’s name,
the organization does not have a fully developed Web site, evidence, some of Mr.
Obama’s advisers said, of just how murky the mission is.
Mr. Plouffe said the group had not settled on a budget or begun serious
fund-raising. The goal is to have a relatively small staff, with representatives
in most, if not every, state, and to make up any shortfall in personnel with the
use of technology.
There is a clear interest in keeping the Internet-based political machinery that
made Mr. Obama’s brand so iconic and that helped him raise record amounts. The
new group’s initials, O.F.A., conveniently also apply to his Obama for America
campaign. And the desire for the Obama organization to live on was voiced in a
meeting of organizers in Chicago after Election Day, and echoed at 4,800 house
meetings in December and in a survey completed by 500,000 Obama supporters.
Still, sensitive to ruffling feathers even among fellow Democrats wary of Mr.
Obama’s huge political support, Mr. Obama’s aides emphasized that the effort was
not created to lobby directly or pressure members of Congress to support Mr.
Obama’s programs.
“This is not a political campaign,” Mr. Plouffe said. “This is not a ‘call or
e-mail your member of Congress’ organization.”
Instead, Mr. Plouffe said the aim was to work through influential people in
various communities as a way of building public opinion.
“So it’s: ‘Here’s the president’s speech today on the economy. Here are some
talking points,’ ” he said. “This was a very under-appreciated part of our
campaign. If someone who has never been involved in politics before — or is an
independent or a Republican — makes this case with their circle of people, that
has more impact.”
The operation is being run from borrowed desks on the third floor of the D.N.C.
headquarters on Capitol Hill, led by organizers chosen, Mr. Plouffe said,
because of skills they demonstrated during the campaign. The head of the group
is Mitch Stewart, a low-key operative who helped run Mr. Obama’s effort in three
critical states — Iowa and Indiana in the primary season and Virginia in the
general election. Another important person in the operation is Jennifer O’Malley
Dillon, the new executive director of the Democratic National Committee, who was
the battleground states director for Mr. Obama in his campaign.
And there will be clear coordination between this independent operation at the
Democratic National Committee and a communications arm being set up at the White
House, under Macon Phillips, the “new media” director for Mr. Obama’s
administration.
Mr. Phillips was an Internet strategist with Blue State Digital, a private firm
closely tied to Mr. Obama’s campaign. His team signaled the new direction Mr.
Obama is bringing with a redesigned White House Web site that was introduced
shortly after Mr. Obama was sworn in and is modeled after his campaign site. It
will be continually updated to add presidential orders and blog postings that
make the case for administration policy, often echoed by talking points that
Organizing for America is sending to supporters.
In an interview, Mr. Phillips, 30, said the site would give the White House
another way to reach the public without having to rely on the mainstream news
media.
“Historically the media has been able to draw out a lot of information and
characterize it for people,” he said. “And there’s a growing appetite from
people to do it themselves.”
The approach is causing some concern among news media advocates, who express
discomfort with what effectively could become an informational network reaching
13 million people, or more, with an unchallenged, governmental point of view.
“They’re beginning to create their own journalism, their own description of
events of the day, but it’s not an independent voice making that description,”
said Bill Kovach, the chairman of the Committee of Concerned Journalists. “It’s
troublesome until we know how it’s going to be used and the degree to which it
can be used on behalf of the people, and not on behalf of only one point of
view.”
The undertaking will require Mr. Obama’s aides to wedge technology that worked
for them in the campaign into the infrastructure of the White House, with its
relatively older technology and security restrictions. Where Mr. Obama’s
campaign was free to use Facebook, instant messaging and Twitter, among other
forms of communication, the White House faces more constraints. With every note
part of the historical record, and new scrutiny on every communication, staff
members are unable to access public instant messaging accounts and social
networking sites from their desks.
The administration’s Web team has a YouTube channel, but it is already
exhibiting the dangers for a White House in the Wild West of the Internet: a
page showing Mr. Obama’s inauguration address is littered with offensive
commentary from users.
In campaigns, candidates control multimillion-dollar advertising budgets and
organizations in 50 states. When they take office, they have had to put their
own stamp on existing party organizations, and to rely largely on the news media
to communicate with the public. Though he comes to the task with the advantage
of a team that proved innovative in using technology and communications advances
to reshape electoral politics, Mr. Obama’s challenge is not totally different
from the one that faced his predecessors.
“The problem that you have is, you come off a campaign — where there is an
infrastructure and a director in every state — and then you have nothing,” said
Sara Taylor, a White House political director for Mr. Bush. “You have allied
organizations, but they don’t report to you, so you’re relying on allies to be
supportive when you don’t have control of those organizations.”
Mr. Obama’s aides acknowledged that after two long years there were also some
concerns about “list fatigue.” Mr. Obama, the party and the inaugural committee
have reached out to his supporters on the e-mail list so frequently — for money,
for input, for help in persuading their neighbors to vote — that some want to
give it a rest before cranking it up again.
Even some of Mr. Obama’s most enthusiastic foot soldiers understand the
sentiment.
“It’s kind of like we’re spent right now,” said Dr. Robert Gitchell, who
campaigned for Mr. Obama in Ames, Iowa. But, “once that fire is lit” in
supporters, he said, “it’s easy to trigger them all again.”
Melding Obama’s Web to a
YouTube Presidency, NYT, 26.1.2009,
http://www.nytimes.com/2009/01/26/us/politics/26grassroots.html
Google plans to make PCs history
Industry critics warn of danger in giving internet leader more power
Sunday 25 January 2009
The Observer
David Smith, technology correspondent
This article was first published on guardian.co.uk at 00.01 GMT on Sunday 25
January 2009.
It appeared in the Observer on Sunday 25 January 2009 on p22 of the News
section.
It was last updated at 13.06 GMT on Monday 26 January 2009.
Google is to launch a service that would enable users to access their
personal computer from any internet connection, according to industry reports.
But campaigners warn that it would give the online behemoth unprecedented
control over individuals' personal data.
The Google Drive, or "GDrive", could kill off the desktop computer, which relies
on a powerful hard drive. Instead a user's personal files and operating system
could be stored on Google's own servers and accessed via the internet.
The long-rumoured GDrive is expected to be launched this year, according to the
technology news website TG Daily, which described it as "the most anticipated
Google product so far". It is seen as a paradigm shift away from Microsoft's
Windows operating system, which runs inside most of the world's computers, in
favour of "cloud computing", where the processing and storage is done thousands
of miles away in remote data centres.
Home and business users are increasingly turning to web-based services, usually
free, ranging from email (such as Hotmail and Gmail) and digital photo storage
(such as Flickr and Picasa) to more applications for documents and spreadsheets
(such as Google Apps). The loss of a laptop or crash of a hard drive does not
jeopardise the data because it is regularly saved in "the cloud" and can be
accessed via the web from any machine.
The GDrive would follow this logic to its conclusion by shifting the contents of
a user's hard drive to the Google servers. The PC would be a simpler, cheaper
device acting as a portal to the web, perhaps via an adaptation of Google's
operating system for mobile phones, Android. Users would think of their computer
as software rather than hardware.
It is this prospect that alarms critics of Google's ambitions. Peter Brown,
executive director of the Free Software Foundation, a charity defending computer
users' liberties, did not dispute the convenience offered, but said: "It's a
little bit like saying, 'we're in a dictatorship, the trains are running on
time.' But does it matter to you that someone can see everything on your
computer? Does it matter that Google can be subpoenaed at any time to hand over
all your data to the American government?"
Google refused to confirm the GDrive, but acknowledged the growing demand for
cloud computing. Dave Armstrong, head of product and marketing for Google
Enterprise, said: "There's a clear direction ... away from people thinking,
'This is my PC, this is my hard drive,' to 'This is how I interact with
information, this is how I interact with the web.'"
Google plans to make PCs
history, O, 25.1.2009,
http://www.guardian.co.uk/technology/2009/jan/25/google-drive-gdrive-internet
Slicing Decades of Video for New Life on the Web
January 26, 2009
The New York Times
By BRIAN STELTER
SILVER SPRING, Md. — Media companies are rushing to repackage their videos
for the Internet, and some say they can hardly keep up with advertiser demand
for more. Video clips of TV shows and behind-the-scenes outtakes are omnipresent
online — but how do they get there?
Part of the answer is here, at the headquarters of Discovery Communications,
where a small team of editors mines the 23-year-old video vault of the Discovery
Channel for animal attacks, dinosaur animations and scientific oddities. Old
shows that ordinarily would not be repeated on Discovery or its other cable
channels can be repackaged online, turning every week into “Shark Week,” three
minutes at a time.
As users spend more time watching videos with advertisements attached, they are
fast becoming an incremental moneymaker for media companies. While the young
medium is not impervious to the economic slowdown, the research firm eMarketer
forecasts a 45 percent gain in online video spending in 2009, evidence of the
sharp rise in video production for the Web.
Perhaps that explains why the words “brighter digital future” are scribbled in
blue ink on a whiteboard next to Josh Ferg’s desk. Mr. Ferg is one of eight
producer-editors, or preditors for short, who create bite-size video for the Web
at Discovery.
Despite the unfortunate job title — “I think ‘Dateline NBC’ has kind of ruined
it,” Mr. Ferg joked, referring to the newsmagazine’s “To Catch a Predator”
franchise — Discovery views the team as an important part of its Internet
strategy. The producer-editors made about 4,500 videos for Discovery’s Web sites
last year, helping the company record eight million video views in November.
While the online advertising market has slowed considerably because of the weak
economy, the executive vice president for digital media at Discovery, Josh
Freeman, said advertisers’ demand for video remained robust. Asked whether the
ads were lagging behind the content creation, he responded: “In video? Not a
chance.”
When Mr. Freeman arrived from AOL in mid-2007, he said, he concluded that
Discovery “was just leaving money on the table” in online video. Now, he says,
the company is playing catch-up.
To a greater extent than most media companies, Discovery owns the global rights
to the content it broadcasts. Because the company owns 13 networks in the United
States, including TLC, Animal Planet and the Science Channel, it has untold
thousands of hours of footage. And because many of its TV episodes are timeless,
the clips can still be relevant to Internet users years after their original
broadcast.
“Cheetahs are still killing gazelles the same way they did 3,000 years ago,”
Doug Craig, the senior vice president for digital media production, said, “and
on top of that, we don’t have to pay residuals.”
To that end, Discovery has added six temporary employees to “maximize the
library,” Mr. Craig said. They are repackaging old shows into short clips for
the how-to Web site HowStuffWorks, a recent acquisition by Discovery, and
Discovery’s other platforms.
That gives Mr. Ferg and the other full-time producer-editors time for more
complex projects. Sometimes they blend several videos to create original series
with new graphics and narration. Recent examples include “Jaws and Claws,” about
the relationship between predator and prey, and “Strange Science,” about all
sorts of bizarre phenomena. The Science Channel recently shortened the latter
segments into 30-second vignettes.
Almost every video is shorter than five minutes. “Killer Clips,” a series of 30-
to 40-second clips of animal takedowns, have proved especially popular on the
Animal Planet Web site. But Mr. Ferg avoids the term clipping because, he says,
it oversimplifies the process. “It’s always about a story,” he said, whether
that story is an hour or a minute long.
When the producer-editors want to repackage shows from long ago, the continuing
digitization of the Discovery archives allows them to mine the vault ever
deeper. An archive in Sterling, Va., stores 1.3 million tapes of old episodes;
when a producer wants to clip something from one of those tapes, it is brought
to an editing center a few blocks from Discovery’s headquarters and a digital
copy is created.
All of the shows are fodder for online clips. Mr. Freeman particularly enjoys
the super-slow-motion “Time Warp” videos that show the impact of a boxer’s punch
or a burst of fireworks. The half-hour show lends itself well to one-minute
variations.
Some of the videos seem destined for wide popularity. Placing them on sites like
YouTube clearly helps.
The Discovery series “MythBusters” is probably the most popular show for clips.
A video of one of the co-hosts, Adam Savage, inhaling helium and explaining the
voice-adjusting effects has attracted more than a million views on YouTube. In
the coming months, Discovery will begin selling ads for its videos on YouTube,
adding another source of revenue for the company.
On a recent day, Discovery.com’s short videos featured ads from consumer
products companies, electronics makers and the United States Army. The online
video industry continues to suffer from a lack of specified ad formats and
standardized measurements, but Mr. Freeman is optimistic about ad money.
“Those dollars are going to come,” he said. “I want to be there when they do.”
Slicing Decades of Video
for New Life on the Web, NYT, 25.1.2009,
http://www.nytimes.com/2009/01/26/technology/internet/26vault.html
Prototype
Cellphones as Credit Cards? Americans Must Wait
January 25, 2009
The New York Times
By LESLIE BERLIN
IMAGINE a technology that lets you pay for products just by waving your
cellphone over a reader.
The technology exists, and, in fact, people in Japan have been using it for the
last five years to pay for everything from train tickets to groceries to candy
in vending machines. And in small-scale trials around the world, including in
Atlanta, New York and the San Francisco Bay Area, nearly everyone has liked
using this form of payment.
But consumers in the United States won’t be able to wave and pay with their
cellphones anytime soon: The myriad companies that must work together to give
the technology to the masses have yet to agree on how to split the resulting
revenue.
“In Japan it was easier,” explains Gerhard Romen, director for corporate
business development at Nokia. “It was just the major guys saying, ‘This is how
it will be.’ ” A single carrier, NTT DoCoMo, accounted for more than half the
Japanese market at the time the system was rolled out and thus had significant
leverage with financial institutions and handset manufacturers.
This is not the case in the United States. For such payments to work here,
cellphone manufacturers, carriers, financial institutions and retailers must all
play roles. There also must be some sort of intermediary that is trusted by both
the financial institutions and the carriers to activate the virtual credit cards
inside the phone.
One problem is that anyone using a credit card inside a cellphone is
simultaneously a customer of the financial institution and of the carrier. “At
the end of the day, the question is, ‘Who pays whom and how much?’” Mr. Romen
says. “The carriers and the banks need to get their act together on payment.” He
adds that the back-and-forth is a necessary step in the creation of a complex
system.
Short-range technology, called N.F.C., for Near Field Communication, enables a
phone to talk to an electronic reader. It is already in widespread use — though,
outside Japan, often not in phones.
In London, for example, the technology is embedded in the “Oyster” cards used to
access the transportation system. The technology is also used in credit cards
like payWave from Visa and PayPass from MasterCard that are waved over readers,
rather than swiped through them.
For a phone, the technology to store account information securely is advanced
enough so that several different virtual cards can be placed inside the phone;
users can select an account by using the screen.
Account information can be embedded in the telephone or on a SIM card or microSD
card, but no call over a network is needed to send the data. Proximity is the
key: for the payment to work, the phone needs to be within a few centimeters of
the reader.
The idea of equipping a cellphone with virtual credit cards worries some people;
phones, after all, are easily lost or stolen. But Simon Pugh, group head of the
mobile payments group at MasterCard Worldwide, said that if the phone were lost,
the consumer could call the bank — using another phone, of course — to disable
the account. He also said that consumers could choose to protect the payment
part of their phone with an access code, but he added that the payment would
also be secure even without such measures.
The risk of account fraud from mobile payments is “small,” according to Kevin
Fu, an assistant professor of computer science at the University of
Massachusetts, Amherst, who in 2006 uncovered several security holes in credit
cards that are waved rather than swiped. Credit-card companies say that these
problems have been fixed.
Mr. Fu is more concerned about privacy. He says that it may be possible to get
personal information, like a person’s name, from credit-card account data on a
mobile phone. Nonetheless, he predicts that with time, “these N.F.C. phones will
become one of the best ways to do mobile payments.”
It is almost certain that mobile-phone payments will eventually come to the
United States. After all, the technology promises something for everyone
involved: Credit-card companies would have a new way to attract and keep
customers and would save money by no longer sending cards through the mail.
Carriers would enjoy another source of revenue. Retailers would benefit from a
faster checkout process, and may find that people buy more when they pay with
their phones.
And according to Joanne Trout, vice president of worldwide communications for
MasterCard Worldwide, there will not be an additional fee for consumers to use
credit cards on their phones.
Consumers, too, would probably like using their cellphone credit cards, if
wave-and-pay were secure and widely available. It may be another instance of the
phenomenon, so common in technology, of not knowing we want something until we
have it. “People really do like it,” said Key Pousttchi, head of the Wi-mobile
research group at the University of Augsburg in Germany. “It is easy. It is
convenient. It helps you.”
The group has surveyed thousands of people who have participated in mobile-phone
trials around the world.
Mr. Pousttchi says he expects that by 2012, most phones will contain the N.F.C.
technology that makes wave-and-pay possible. But he cautions that this doesn’t
necessarily mean that Americans will be paying with their cellphones in three
years. For that to happen, all the players will have to work together to define
standards, determine revenue-sharing, expand the network of electronic readers
and think through the other parts of what he calls “this 2,000-piece puzzle.”
The NFC Forum, an industry association based in Wakefield, Mass., whose 150
members include manufacturers, carriers and financial institutions, is a good
start. Mr. Romen and Mr. Pugh are both vice chairmen of the group.
Nonetheless, Mr. Pousttchi warns, “it is completely possible nothing will happen
in mobile payments in the next five years if everybody keeps thinking only about
their own piece of the puzzle.”
Leslie Berlin is project historian for the Silicon Valley Archives at Stanford.
Cellphones as Credit
Cards? Americans Must Wait, NYT, 25.1.2009,
http://www.nytimes.com/2009/01/25/business/25proto.html
Worm Infects Millions of Computers Worldwide
January 23, 2009
The New York Times
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions
of personal and business computers in what seems to be the first step of a
multistage attack. The world’s leading computer security experts do not yet know
who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through
corporate, educational and public computer networks around the world. Known as
Conficker or Downadup, it is spread by a recently discovered Microsoft Windows
vulnerability, by guessing network passwords and by hand-carried consumer
gadgets like USB keys.
Experts say it is the worst infection since the Slammer worm exploded through
the Internet in January 2003, and it may have infected as many as nine million
personal computers around the world.
Worms like Conficker not only ricochet around the Internet at lightning speed,
they harness infected computers into unified systems called botnets, which can
then accept programming instructions from their clandestine masters. “If you’re
looking for a digital Pearl Harbor, we now have the Japanese ships steaming
toward us on the horizon,” said Rick Wesson, chief executive of Support
Intelligence, a computer security consulting firm based in San Francisco.
Many computer users may not notice that their machines have been infected, and
computer security researchers said they were waiting for the instructions to
materialize, to determine what impact the botnet will have on PC users. It might
operate in the background, using the infected computer to send spam or infect
other computers, or it might steal the PC user’s personal information.
“I don’t know why people aren’t more afraid of these programs,” said Merrick L.
Furst, a computer scientist at Georgia Tech. “This is like having a mole in your
organization that can do things like send out any information it finds on
machines it infects.”
Microsoft rushed an emergency patch to defend the Windows operating systems
against this vulnerability in October, yet the worm has continued to spread even
as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security
firm, estimated that about 30 percent of Windows-based computers attached to the
Internet remain vulnerable to infection because they have not been updated with
the patch, despite the fact that it was made available in October. The firm’s
estimate is based on a survey of nine million Internet addresses.
Security researchers said the success of Conficker was due in part to lax
security practices by both companies and individuals, who frequently do not
immediately install updates.
A Microsoft executive defended the company’s security update service, saying
there is no single solution to the malware problem.
“I do believe the updating strategy is working,” said George Stathakopoulos,
general manager for Microsoft’s Security Engineering and Communications group.
But he added that organizations must focus on everything from timely updates to
password security.
“It’s all about defense in depth,” Mr. Stathakopoulos said.
Alfred Huger, vice president of development at Symantec’s security response
division, said, “This is a really well-written worm.” He said security companies
were still racing to try to unlock all of its secrets.
Unraveling the program has been particularly challenging because it comes with
encryption mechanisms that hide its internal workings from those seeking to
disable it.
Most security firms have updated their programs to detect and eradicate the
software, and a variety of companies offer specialized software programs for
detecting and removing it.
The program uses an elaborate shell-game-style technique to permit someone to
command it remotely. Each day it generates a new list of 250 domain names.
Instructions from any one of these domain names would be obeyed. To control the
botnet, an attacker would need only to register a single domain to send
instructions to the botnet globally, greatly complicating the task of law
enforcement and security companies trying to intervene and block the activation
of the botnet.
Computer security researchers expect that within days or weeks the bot-herder
who controls the programs will send out commands to force the botnet to perform
some as yet unknown illegal activity.
Several computer security firms said that although Conficker appeared to have
been written from scratch, it had parallels to the work of a suspected Eastern
European criminal gang that has profited by sending programs known as
“scareware” to personal computers that seem to warn users of an infection and
ask for credit card numbers to pay for bogus antivirus software that actually
further infects their computer.
One intriguing clue left by the malware authors is that the first version of the
program checked to see if the computer had a Ukrainian keyboard layout. If it
found it had such a keyboard, it would not infect the machine, according to
Phillip Porras, a security investigator at SRI International who has
disassembled the program to determine how it functioned.
The worm has reignited a debate inside the computer security community over the
possibility of eradicating the program before it is used by sending out
instructions to the botnet that provide users with an alert that their machines
have been infected.
“Yes, we are working on it, as are many others,” said one botnet researcher who
spoke on the grounds that he not be identified because of his plan. “Yes, it’s
illegal, but so was Rosa Parks sitting in the front of the bus.”
This idea of stopping the program in its tracks before it has the ability to do
damage was challenged by many in the computer security community.
“It’s a really bad idea,” said Michael Argast, a security analyst at Sophos, a
British computer security firm. “The ethics of this haven’t changed in 20 years,
because the reality is that you can cause just as many problems as you solve.”
Worm Infects Millions
of Computers Worldwide, NYT, 23.1.2009,
http://www.nytimes.com/2009/01/23/technology/internet/23worm.html
|